APIs are critical for sharing business data. If they are not protected, things can go wrong very fast. The FlexBooker, a scheduling and booking platform, data breach incident proved this clearly. Sensitive data, such as usernames, transaction details, and IP addresses of millions of app users was compromised because the API was not secure.
The incident also underscores the importance of securing APIs and managing data visibility to avoid such attacks in the future.
In this blog, we’ll explore the causes of unsafe consumption of APIs, associated risks, and best practices for prevention.
Understanding Unsafe Consumption of APIs Threats
APIs are the cornerstone of modern application architecture, but if they are exposed to any vulnerability, this can negatively impact business resiliency. Considering the severity of the risk, unsafe consumption of APIs is featured in the #10th spot in the list of OWASP API Top 10 risks.
Learn more about OWASP API Top 10 Risks and prevention tips
The worrying news is the risk is increasing. According to Gartner, since APIs are the primary means of accessing enterprise data and functionality, they’re used frequently, which makes them a prime target for attackers.
Common API Security Risks
APIs serve as gateways to data and services in applications. But if consumed in the wrong way, the vulnerabilities can compromise entire systems.
Common API security risks include weak authentication, excessive data exposure, and lack of rate-limiting mechanisms. These threats can be minimized if developers enforce strict security measures, such as proper authentication, encryption, and regular security audits.
The Role of Trust in API Interactions
Trust is the foundation of secure API interactions. When systems integrate third-party APIs, they depend on providers to enforce strong security measures such as authentication, encryption, and access controls.
Lack of proper security measures can lead to attacks and data breaches. Clear documentation, consistent uptime, and adherence to industry standards help establish this trust. Without this trust, businesses may hesitate to adopt APIs.
Common Causes of Unsafe Consumption of APIs
Below, we have presented a list of some of the common causes of unsafe consumption of API risks are:
1. Insecure Communication Channels
Interacting with external APIs over unencrypted protocols, such as HTTP instead of HTTPS, exposes sensitive data for interception or man-in-the-middle (MitM) attacks. Let’s understand this with the following example of Python code snippet:
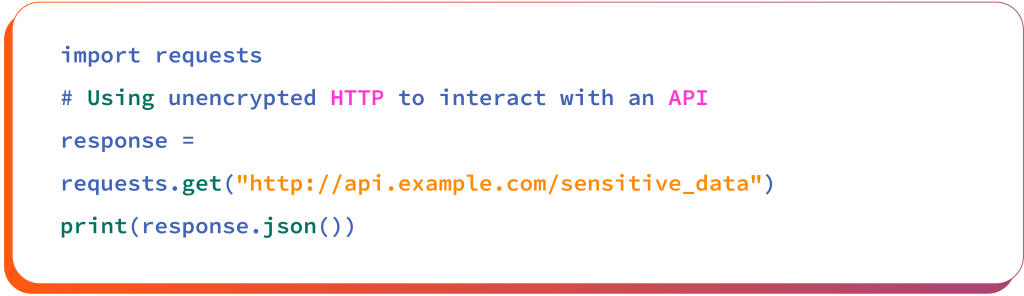
From the above code snippet, the data (e.g., authentication tokens, user credentials) is transmitted in plaintext, which makes it vulnerable to eavesdropping or man-in-the-middle (MitM) attacks. Attackers can easily intercept this transmitted data and steal sensitive information.
2. Insufficient Input Validation/Sanitization
Failing to validate, sanitize, or normalize data ingested from third-party APIs can lead to injection attacks (e.g., SQLi, XSS). Let’s understand this with a following example:
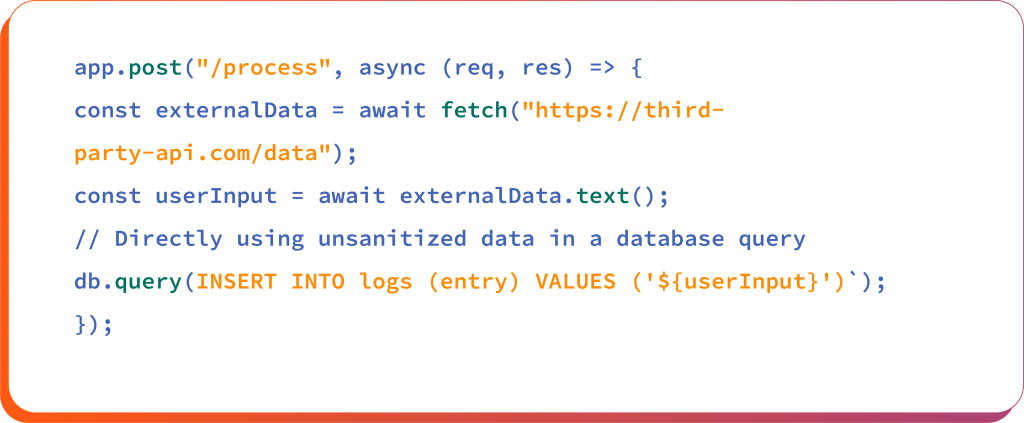
If user input contains malicious payloads, such as “DROP TABLE logs–”, it can enable an SQL injection vulnerability that may potentially allow attackers to perform unauthorized actions, such as deleting data or corrupting the database.
Several organizations have faced breaches due to inadequate API input validation. For example, BitGrail experienced a massive breach and lost a significant amount of cryptocurrency. The incident occurred when client-side balance checks were bypassed, allowing fraudulent withdrawals by attackers.
To prevent such failures, organizations should enforce strict server-side validation. They should check the format and context of all inputs and reject any malformed data.
3. Unvalidated Redirection Handling
Blindly trusting redirection instructions from external APIs without verifying the legitimacy of the endpoint can be risky. It can redirect traffic to malicious domains or phishing sites. Unvalidated redirect occurs when the application does not verify whether the URL redirects to a trusted source.
For example, suppose you have a domain, “example.com,” and your site has an unvalidated redirect vulnerability. An attacker can alter its parameter value and perform CRLF injection (Carriage Return Line Feed) to redirect users to a malicious location.
4. Unrestricted Resource Allocation
Lack of quotas or throttling for processing third-party API responses, may potentially risk resource exhaustion, such as memory, CPU and denial-of-service (DoS) attacks.
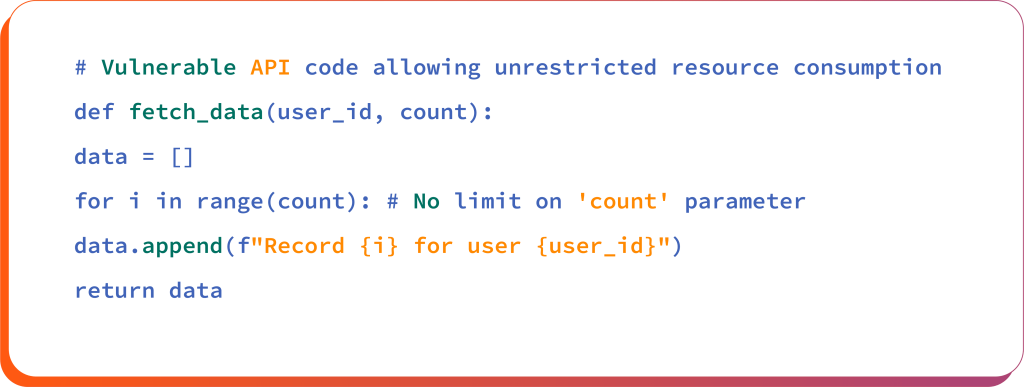
This code lets users request any number of records without limits, risking server overload and denial of service from excessive resource consumption.
5. Unencrypted Data Transmission
Data transmitting over HTTP without TLS is insecure as it travels. Hackers can intercept login details, credit card numbers, or other sensitive details. It can cause compliance violations. Therefore, always use a combination of HTTPS HTTP + TLS to ensure sensitive information is locked.
Real-World Examples: Unsafe API Consumption Exploits
Example #1: Facebook–Cambridge Analytica
This incident happened because Facebook’s Graph API allowed third-party apps to collect much more personal data than needed. There was also a lack of proper consent enforcement and weak checks on app developers, which made it easier for misuse to happen.
Facebook did not realize how weak API controls could lead to large-scale data harvesting. The breach damaged public trust, brought worldwide regulatory attention, and resulted in multi-billion-dollar fines. Better data minimization and ongoing audits of third-party apps could have stopped this from happening.
Example #2: Peloton API Vulnerability
The breach occurred because Peloton left an API endpoint open without proper authentication, allowing unauthorized users to access sensitive member details. The lack of basic security practices such as authentication, authorization, and rate limiting exposed personal demographics and fitness activity data.
This lack of oversight attracted criticism of Peloton’s approach to data protection and raised doubts about its overall security posture.
Implementing strict authentication, security testing before release, and continual vulnerability monitoring could have prevented the leak and safeguarded user privacy.
Example #3: T-Mobile Data Breach
The breach occurred by an insecure API configuration. Attackers used this loophole to extract highly sensitive information like Social Security numbers and driver’s license details.
The root cause of the incident was weak access control combined with inadequate logging and monitoring of API activities. Neglecting regular security tests and mismanaging API exposure left massive amounts of customer data unprotected.
The incident caused severe reputational damage, hefty regulatory penalties, and identity theft risks for customers. Proper API hardening and real-time anomaly detection could have prevented it.
Common Attack Techniques Using Unsafe Consumption of APIs
Integrating APIs without proper security can be a security hazard. Here are five simple ways attackers take advantage of these weaknesses.
- API response manipulation: Attackers gain unauthorized access to data and modify it when APIs send responses to the application. This tricks the system into a trap, causing it to do things it should not do, such as showing fake information or an incorrect account balance. It can cause security problems or mess up data.
- Insecure input parsing: If an app fails to validate inputs before sending them to an API, attackers can send malicious data. This might make the API run harmful commands or access data it shouldn’t, causing data leaks or system compromise.
- Poor error handling: Some APIs give detailed error messages that may reveal secrets about how the system or database works. Attackers can capture this information to find weak spots and launch attacks.
- API key misuse: API keys let apps use APIs securely, but if they’re stored poorly or sent over unsafe connections, attackers can misuse them to steal information. They can sneak into the API and cause trouble.
- Injection attacks through API consumption: When apps don’t sanitize inputs sent to an API, attackers can inject harmful code or commands. This can let them steal data, change things, or even take over the system.
Strategies to Prevent Unsafe Consumption of APIs
Security teams need to adopt credible strategies to safeguard against the API risks associated with third-party API integrations. Implementing the following best practices will help mitigate vulnerabilities effectively.
Strict Input Validation
- Use comprehensive validation mechanisms to check data types, lengths, formats, and ranges before processing.
- Ensure outgoing data is properly formatted to avoid unintended effects.
- Implement allowlist-based data validation.
- Accept only predefined valid inputs to minimize risks of unauthorized access.
- Adopt a whitelisting approach that only accepts predefined, expected input patterns.
Token-Based Authentication
- Use robust token-based authentication mechanisms like JWT (JSON Web Tokens) with short expiration times and secure signing.
- Implement secure token authentication mechanisms like multi-factor authentication.
- Ensure tokens are encrypted and cannot be tampered.
- Rotate tokens frequently and invalidate them immediately after use or suspected compromise.
Learn in-depth about API authentication mechanisms, methods and best practices
Secure Third-Party Integration
- Make sure that data received from third-party APIs is authentic and unaltered to prevent malicious tampering.
- Limit API request rates and monitor usage to prevent abuse, such as Denial-of-Service (DoS) attacks or excessive resource consumption.
Error Handling And Logging
- Use generic error messages to prevent information leakage like “An error occurred” to avoid exposing sensitive system or application details to attackers.
- Consolidate logs in a secure system to monitor, detect, and respond to unusual activities or security threats effectively.
Rate Limiting and Throttling
- Configure intelligent rate limiting to prevent denial-of-service attacks and manage API resource consumption.
- Define granular throttling rules based on user roles, IP addresses, and request types.
- Implement progressive rate limits that dynamically adjust based on traffic patterns.
- Use exponential backoff mechanisms for repeated failed attempts.
Encryption of Sensitive Data
- Enforce end-to-end encryption for all API communications using strong protocols like TLS 1.3.
- Implement field-level encryption for sensitive data, ensuring that even if data is intercepted, it remains unreadable.
- Use secure key management practices.
- Implementing encryption at both transport and application layers.
Implement Least Privilege Access Control
- Design granular role-based access control (RBAC) systems that provide minimal necessary permissions.
- Enforce strict access controls.
- Verify user roles and permissions before allowing any action.
- Regularly audit and update access rights and remove unnecessary privileges.
Sanitize and Validate API Responses
- Sanitize and validate API responses from third-party services.
- Implement robust parsing mechanisms that strip potentially harmful content.
- Validate response schemas, and ensure data integrity.
- Reject or transform responses that don’t meet predefined security and structural criteria.
Use API Gateways and Proxy Services
Leverage API gateways as a protective layer between your applications and external APIs. These gateways can provide additional security features like request/response transformation, authentication, rate limiting, and threat detection. They act as a centralized point for managing and securing API interactions.
Regular Security Audits and Penetration Testing
Regular security audits can identify weaknesses in advance . Here are some ways that can be helpful:
- Conduct periodic security assessments and penetration testing specifically targeting API endpoints.
- Use automated scanning tools and manual ethical hacking techniques to identify vulnerabilities.
- Simulate real-world attack scenarios to uncover potential weaknesses in authentication, data handling, and access control mechanisms.
Implement Secure Webhook Handling
- Implement strict verification mechanisms.
- Validate webhook origins using secure tokens.
- Implement IP whitelisting.
- Use cryptographic signatures to ensure the integrity of incoming webhook requests.
- Implement timeout and retry mechanisms with proper error handling.
Best Practices for Teams And Organizations
Conduct API Security Audits
- Regularly review API integration endpoints for unsafe data handling. For example, ensure APIs do not expose sensitive data (e.g., Personally Identifiable Information) in error messages.
- Conduct periodic security scans to identify data leakage risks.
- Review third-party API dependencies for security vulnerabilities. For example, use tools like OWASP Dependency-Check or Snyk to scan third-party libraries and APIs for known vulnerabilities.
Implement Continuous Security Testing
- Integrate API fuzz testing to detect unsafe input processing. For example, use tools like ZAP, Burp Suite, or AFL to send unexpected, malformed, or malicious inputs to APIs.
- Enforce contract testing to validate API responses against expected structures. For example, use Pact or Postman to ensure API responses do not contain unexpected or excessive data, preventing data leaks and type mismatches.
Secure Developer Workflows and Training
- Train developers on safe API consumption and response handling. For example, conduct regular security training sessions to educate developers on API security best practices, such as avoiding hardcoded credentials and using environment variables instead.
- Establish secure coding guidelines for API integrations. For example, define best practices such as enforcing OAuth 2.0 for authentication, using rate limiting, and validating all incoming API inputs to prevent injection attacks.
Enforce API Governance
- Define internal policies for consuming third-party APIs securely For example, mandate that all APIs use HTTPS, require authentication, and are vetted for security risks before integration.
- Require security vetting for any new API integration before deployment
For example, conduct penetration testing on APIs before approving their use in production, ensuring they meet organizational security standards.
Automate API Security Monitoring for Unsafe Consumption Risks
- Deploy anomaly detection to flag unexpected API behaviors. For example, use AI-driven security tools like AWS GuardDuty, Datadog, or Splunk to monitor API traffic and detect unusual activity.
- Use API gateways and WAFs to enforce safe API consumption policies. For example, deploy an API gateway like Kong or Apigee to enforce authentication, rate limiting, and request validation.
Conclusion
Securing third-party integrations is essential in today’s interconnected digital landscape. By understanding the risks associated with unsafe consumption of APIs and implementing robust preventive measures, organizations can protect their sensitive data from potential breaches while maintaining trust with their users.
Ignoring unsafe consumption of APIs can pose a significant security threat to organizations. Contact us today to learn how our experts can help.
Frequently Asked Questions (FAQs)
Signs include unencrypted data transmission, frequent error messages, unusual traffic spikes, and unauthorized access attempts, indicating potential vulnerabilities in API interactions.
Ensure secure API consumption by enforcing strict validation, authentication, and monitoring, while implementing allowlist-based rules to restrict unauthorized access.
API monitoring detects anomalies, unauthorized requests, and traffic spikes, enabling proactive responses to mitigate risks before they are exploited.
Tools include API gateways, penetration testing frameworks, anomaly detection systems, and automated vulnerability scanners to identify and address potential security risks.

![Electron research in Desktop apps [Part 1]](https://blog.securelayer7.net/wp-content/uploads/2025/09/electron-research-in-desktop-app-150x150.jpg)