Every API request consumes resources like CPU, memory, network bandwidth, and storage. How much it consumes often depends on user input and how endpoints are designed to process it. When APIs fail to limit request size, frequency, or complexity, they become vulnerable to exploitation. This is a specific type of API security risk.
OWASP has placed this issue at the fourth spot under the Unrestricted Resource Consumption category. This enables brute-force and enumeration attacks against authentication and data access endpoints, including automated attempts to crack credentials or tokens.
In this blog, we’ll understand how unrestricted resource consumption risks occur, their potential consequences, and ways to deal with them.
What is Unrestricted Resource Consumption?
Unrestricted resource consumption is an API vulnerability where systems fail to enforce limits on how much CPU, memory, bandwidth, or processing time a single consumer can use. Attackers can easily exploit this vulnerability by issuing excessive requests, causing services to slow down, become unavailable, or fail entirely.
Threat actors may flood endpoints with high-volume requests or manipulate parameters to force the API to process unusually large workloads, driving up infrastructure costs and destabilising critical services.
Let’s examine a real-world example to understand it better. A few years ago, GitHub faced a massive Distributed Denial of Service (DDoS) attack that peaked at 1.35 terabits per second. Attackers used Memcached, a type of caching system, to overwhelm GitHub’s API infrastructure.
As a result, GitHub had to disrupt operations. The incident underscored the need to implement rate limiting and traffic control mechanisms to prevent such attacks.
Common Attack Vectors of Unrestricted Resource Consumption
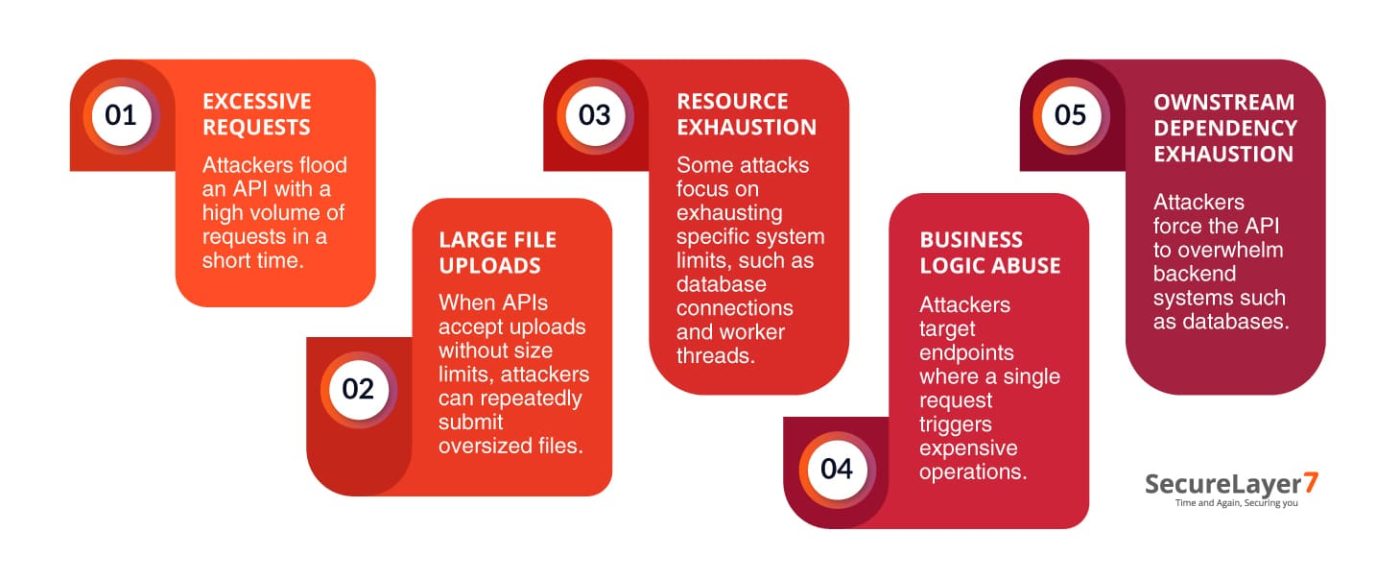
Attackers exploit API4: Unrestricted Resource Consumption vulnerabilities in the following common ways.
- Excessive requests: Attackers can flood an API with a high volume of requests in a short time using automated scripts or botnets, overwhelming the server.
- Large file uploads: When APIs accept file uploads without size limits, attackers repeatedly submit oversized files. This consumes storage, memory, and processing power, eventually degrading performance.
- Resource exhaustion: Some attacks focus on exhausting specific system limits, such as database connections, worker threads, or file descriptors. These limits are easier to hit than CPU or memory caps and can halt critical services.
- Business logic abuse: Attackers target endpoints where a single request triggers expensive operations, such as complex searches, report generation, bulk exports, or deep pagination. These requests look valid but consume disproportionate resources.
- Downstream dependency exhaustion: Attackers force the API to overwhelm backend systems, such as databases, message queues, or third-party services with strict quotas, causing failures outside the API itself.
Types of Resources at Risk
The types of resources at risk from unrestricted consumption include:
- CPU: Excessive processing demands can slow down or halt application performance.
- Memory: A large number of requests can exhaust memory, resulting in crashes or degraded performance.
- Disk Space: Uncontrolled uploads can fill available storage, causing system failures.
- Network Bandwidth: Flooding an API with requests can choke bandwidth, affecting all users and services connected to the network.
Consequences of Unrestricted Resource Consumption
According to OWASP’sOWASP’s Top 10 API Security Risks, Unrestricted Resource Consumption poses serious risks that can undermine an organization’s financial health and operational stability.
Understanding these impacts is essential for developing effective strategies to mitigate risks and safeguard digital assets in an increasingly complex threat landscape.
Denial of Service (DoS)
One of the most immediate threats posed by unrestricted resource consumption is the risk of Denial of Service (DoS) attacks.
In these scenarios, malicious actors exploit application vulnerabilities to flood systems with excessive requests, overwhelming servers and rendering them unavailable to legitimate users.
According to the Cybersecurity and Infrastructure Security Agency (CISA), approximately 70% of organizations reported experiencing at least one DoS attack in the past year.
This disrupts normal business operations and can lead to a cascading effect where other dependent services fail, exacerbating downtime and user frustration.
Financial Implications
The financial implications of such attacks can be staggering. A study by the Ponemon Institute revealed that the average cost of a data breach is around $4.45 million, a figure that can rise dramatically with extended service outages.
Beyond direct losses from halted transactions, organizations may incur additional costs related to incident response, system recovery, and potential regulatory fines if they fail to comply with data protection laws during breaches.
Moreover, reputational damage can lead to long-term customer attrition, further impacting revenue streams.
Operational Risks
Operational risks associated with unrestricted resource consumption are equally concerning. Systems that experience performance degradation due to excessive resource demands can lead to inefficiencies in service delivery.
For instance, critical business functions may slow down or become unresponsive, hindering productivity and affecting employee morale. Additionally, when cybersecurity teams are inundated with managing these resource-related issues, their ability to respond to emerging threats diminishes.
This creates a precarious situation where organizations may become more vulnerable to sophisticated cyberattacks while struggling to maintain operational integrity.
Unrestricted Resource Consumption: Example Scenarios
Here are two example scenarios of Unrestricted Resource Consumption Risks:
Example Scenario #1
A service provider lets customers download files of any size through its API. The files are stored in cloud storage and usually don’t change. To save bandwidth, the provider uses a cache that only supports files up to a size of 15 GB.
When the file grows to 18 GB, it no longer fits in the cache. Every download is served directly from cloud storage instead of the cache.
When many customers download it at once, data transfer usage increases quickly. Without usage alerts or spending limits, the cost spike goes unnoticed until billing.
Example Scenario # 2
A social network has implemented a “forgot password” feature that leverages SMS verification, allowing users to receive a one-time token via SMS to reset their passwords.
When a user clicks on “forgot password,” an API call is initiated from the user’s browser to the back-end API.
Subsequently, the back-end makes a call to a third-party API responsible for delivering the SMS. In this scenario, an attacker creates a script that sends multiple API calls.
As a result, the back-end repeatedly sends an overwhelming number of text messages, causing the company to incur significant losses.
Mitigation Strategies for Unrestricted Resource Consumption
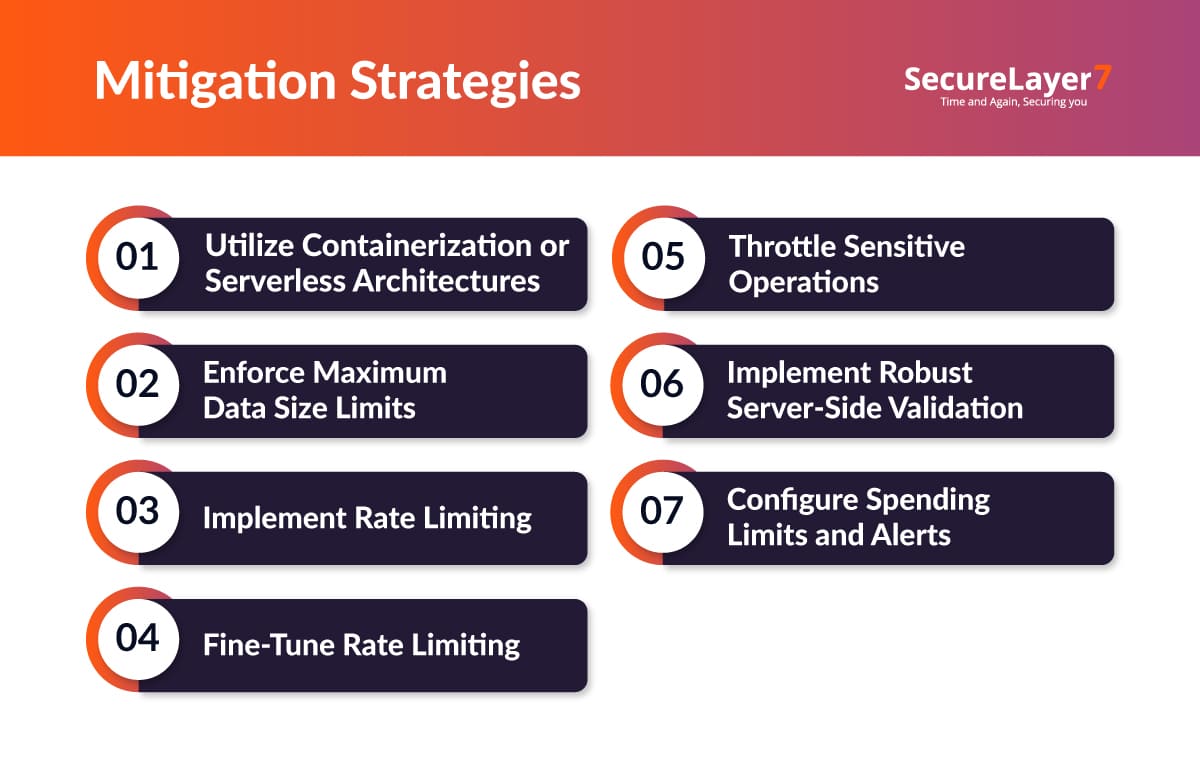
1. Utilize Containerization or Serverless Architectures
Security teams should define strict resource limits for each deployment by leveraging containerization or serverless architectures. This prohibits applications from consuming excessive resources.
For example, serverless functions can automatically scale based on demand while adhering to defined memory and execution time limits, enhancing security and performance.
2. Enforce Maximum Data Size Limits
Define and enforce a maximum data size on all incoming parameters and payloads by setting limits on the maximum length for strings, the maximum number of elements in arrays, and the maximum upload file size.
Establishing clear boundaries for data size helps ensure that APIs remain responsive and can handle legitimate requests without succumbing to overload from malicious input.
3. Implement Rate Limiting
Implement a rate limit on how often a client can interact with the API within a defined timeframe through rate limiting. This practice helps prevent abuse by restricting the number of requests a user can make in a given period.
Controlling traffic flow enables organizations to protect their APIs from being overwhelmed by excessive requests.
Rate limiting is essential for safeguarding against denial-of-service attacks and ensuring fair resource allocation among users.
4. Fine-Tune Rate Limiting
Rate limiting should be fine-tuned based on business needs. Some API endpoints may require stricter policies due to their sensitivity or resource intensity. For instance, endpoints handling financial transactions might necessitate lower thresholds than those serving public data.
Tailoring rate limits according to specific use cases allows organizations to balance security with user experience effectively while minimizing the risk of abuse.
5. Throttle Sensitive Operations
Limit how often a single user or API client can perform sensitive actions, such as validating an OTP, or requesting password resets without using the one-time link. Setting such limits in place protects critical workflows and makes them far harder to abuse.
6. Implement Robust Server-Side Validation
Add proper server-side validation for query string and request body parameters, particularly those controlling the number of records returned in a response. Implementing robust validation ensures that inputs conform to expected formats and limits, preventing attackers from manipulating requests to extract excessive data.
7. Configure Spending Limits and Alerts
To manage costs effectively, configure spending limits for all service providers and API integrations. When setting spending limits is not feasible, organizations should configure billing alerts to monitor usage closely.
Best Practices to Prevent Unrestricted Resource Consumption Risk
To prevent unrestricted resource consumption vulnerabilities, developers should adopt several best practices:
- Ensure all incoming data is validated against expected formats and sanitized to eliminate potentially malicious inputs.
- Employ robust authentication methods using OAuth, API keys and enforce precise authorization controls to restrict access to sensitive resources.
- Utilize API gateways for centralized management of security policies, including rate limiting, authentication, and logging, to streamline security enforcement across all APIs.
- Implement comprehensive logging and monitoring to detect unusual patterns in API usage.
Conclusion
Finally, Unrestricted Resource Consumption poses a significant risk for APIs, potentially resulting in denial-of-service attacks. Therefore, it becomes essential to identify potential threat actors, how they attack, and recognize the vulnerabilities in your systems to mitigate these risks. Furthermore, you must implement the best practices to safeguard your APIs and ensure their reliability.
To further strengthen your security posture, consider partnering with SecureLayer7’s Red Teaming and Penetration Testing team. Get in touch with us to know more.
FAQs
The reason is rate limits often ignore request size, complexity, and business logic. A small number of “valid” requests can still consume excessive resources.
Yes. Attackers frequently use valid accounts or API keys to abuse expensive endpoints while staying under basic rate-limit thresholds.
Endpoints that support search, filtering, bulk operations, file uploads, report generation, or deep pagination are especially vulnerable.



