Privileged Access Management (PAM) is about keeping security-critical accounts in check. These accounts go far beyond regular user logins, connecting directly to critical systems, sensitive data, and the backbone of an organization’s infrastructure. Because of this, they’re a favorite target for attackers, making careful control and monitoring essential.
Various studies have flagged the security risks associated with PAM. The 2024 Verizon Data Breach Investigations Report found that over 70% of breaches involved the misuse of privileged credentials. Privileged accounts make it easier to run operations, but they also carry serious risks. Hackers look for weak, shared, or forgotten accounts to sneak in, escalate their access, and quietly steal data.
This blog explains privileges, credentials, PAM fundamentals, its lifecycle, and best practices to reduce the risks tied to privileged access.
What are privileged accounts?
Privileged accounts possess special administrative rights for defined user roles and only these users can perform critical actions like installing software, changing system settings, managing user accounts, or accessing sensitive data. Even a single compromise can expose critical systems and confidential information.
What Are Privileges in IT Systems?
Privileges are elevated permissions and capabilities granted to users within an information system to carry out various tasks.
It defines what actions can be performed on critical resources such as files, directories, databases, network configurations, or administrative settings and who can perform these actions.
Common examples of privileges include:
- Read
- Write
- Execute
- Modify
- Delete
- Create
- Administrative rights
Privileges are essential for system administration and management tasks, but they can introduce security risks if not properly managed.
Types of Privileged Accounts
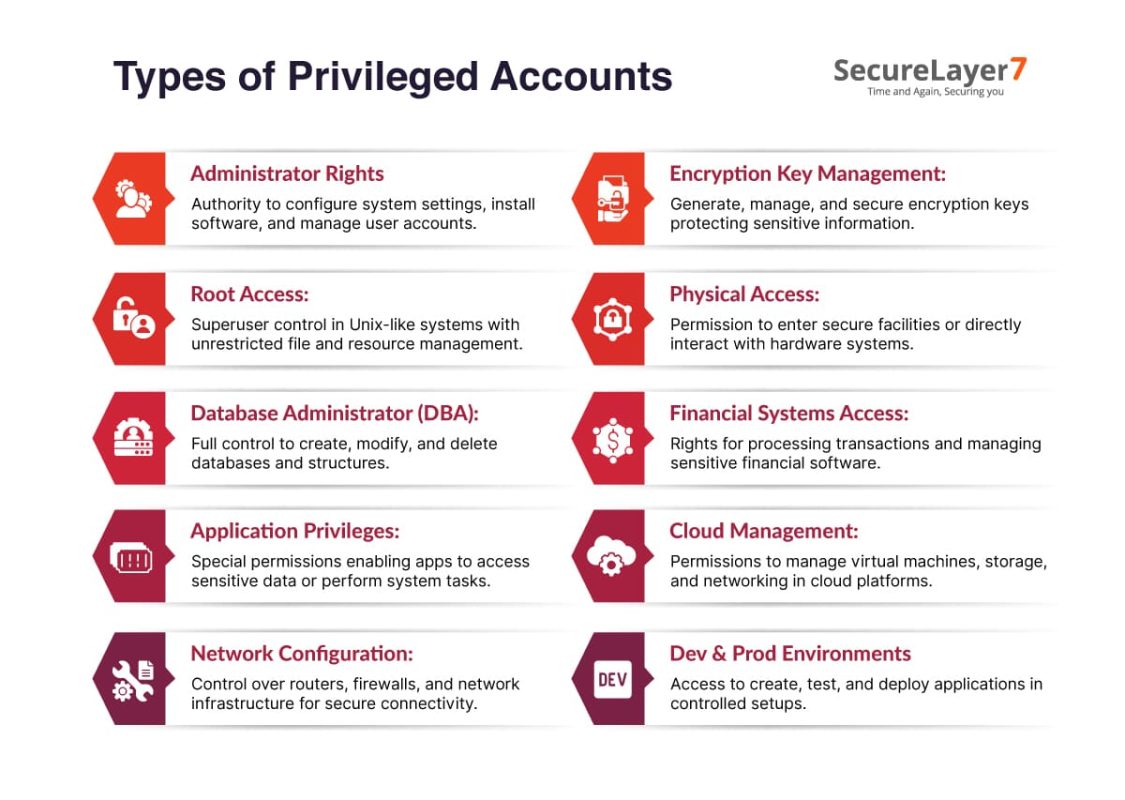
Examples of privileged accounts include:
- Administrator rights ensure authority to configure, manage, and modify system settings, software installations, and user accounts.
- Root access is common in Unix-like operating systems. It has unrestricted control over all files and resources.
- Database administrator (DBA) access provides full control over creating, altering, and deleting databases and their structures.
- Application-level privileges offer elevated permissions required by some specific applications to access sensitive data or perform system-level tasks.
- Network configuration privileges control routers, firewalls, and other network infrastructure.
- Encryption key management provides the ability to generate, manage, and secure encryption keys protecting sensitive information.
- Physical access control is related to permission to enter secure facilities, or interact with hardware components.
- Financial systems access is related to processing transactions and managing financial software.
- Cloud infrastructure management provides permissions for managing virtual machines, storage, and networking in cloud environments.
- Development and production environments allow access to create, test, and deploy software in controlled environments.
What Are Privileged Credentials?
As the name suggests, privileged credentials contain authentication details of privileged accounts. They serve as the digital keys to critical systems, applications, and sensitive data.
Examples of privileged credentials include the following:
- Usernames and passwords for administrator or root accounts
- API keys that connect applications and services
- Cryptographic keys used to encrypt and decrypt sensitive information
- Digital certificates that validate identities and secure communications
- Tokens or SSH keys that authenticate automated processes and scripts
Why Privileged Accounts Become Unmanageable
To keep systems running smoothly, IT teams sometimes give users more access than they really need. These users may keep privileges even after switching roles or leaving the organization. These privileges are often associated with their devices by default.
Here are some other common reasons that create blind spots:
- Too Much Access: When restrictive controls slow users down, admins often give extra privileges to make work easier. Over time, these accounts are forgotten, creating security gaps.
- Privilege Creep: Employees change roles or get promoted but keep access with them they no longer need. Without careful revocation, these old permissions silently accumulate.
- Zombie Accounts: Accounts left behind when employees leave, or rarely used ones, can sit idle for months or years, creating easy targets for attackers.
- Default Credentials: Many service accounts and systems come with built-in passwords. If these defaults aren’t changed, they’re simple for attackers to exploit.
- Static Passwords: Privileged credentials that aren’t rotated or updated are risky. Defaults and long-lasting passwords make accounts vulnerable to misuse.
- Password Sharing: When multiple people use the same admin account or share passwords across systems, it’s hard to track who did what, increasing risk.
- Lack of Monitoring: Even small oversights matter. If account activity isn’t actively monitored, unmanaged accounts can linger unnoticed, becoming gateways for attackers.
What is Privileged Access Management (PAM)?
Privileged access management is defined as a security practice designed to protect an organization’s most valuable assets, including critical systems, applications, and confidential data. This includes strict rules for how privileged accounts are accessed and used. Controls define who can log in, under what conditions, and for how long. This ensures privileges remain secure.
Privileged accounts are omnipresent in the system. Here are some of the benefits of PAMs:
- Administrators, security teams, and developers use PAMs for various purposes, such as configuring servers, monitoring networks, and integrating cloud services.
- PAM helps organizations address various risks by combining policies, technology, and oversight.
- PAM ensures that elevated privileges are used responsibly and only when necessary.
Modern PAMs also need to cover cloud platforms, DevOps, microservices, and RPA. PAM is applicable to all human-to-machine and machine-to-machine scenarios, making it a critical service for safeguarding sensitive credentials and operations.
Understanding PAM Lifecycle
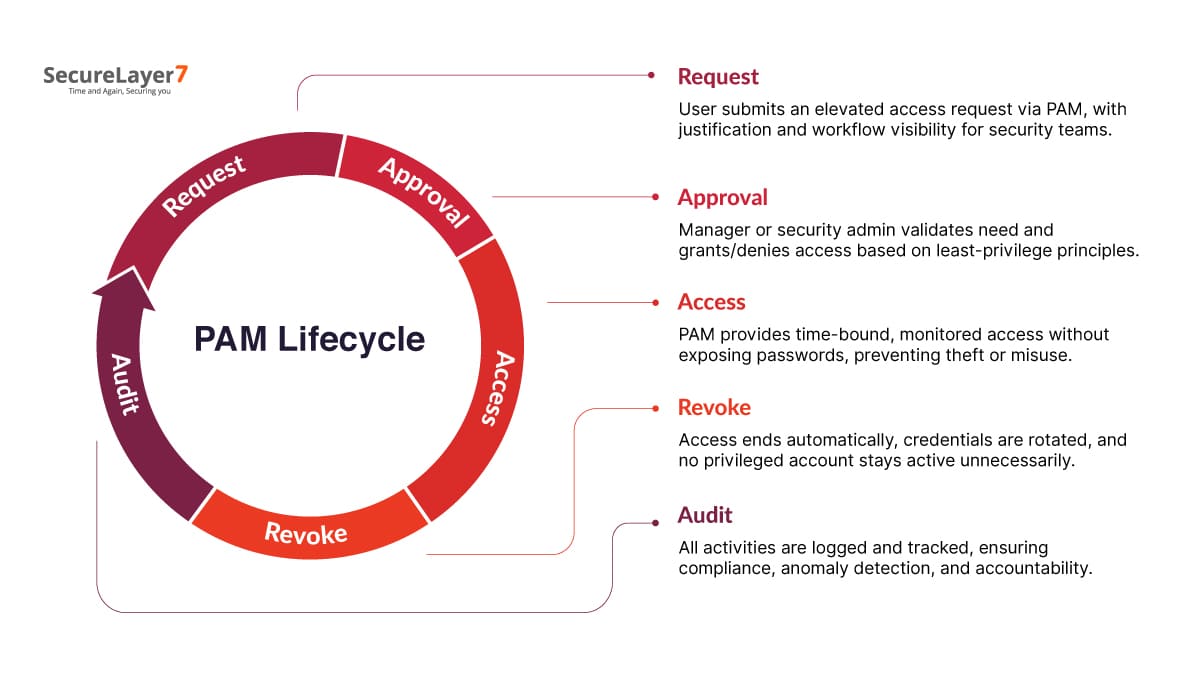
A typical PAM lifecycle consists of:
- Request: A user requests enhanced access for a specific task. The request is submitted through the PAM system, ensuring that no privileged access is granted without proper justification, documentation, and workflow visibility for security teams.
- Approval: The request is reviewed and either granted or denied. Approval is typically handled by a manager or security administrator, who validates the user’s need and applies least-privilege principles to minimize unnecessary risk exposure.
- Access: PAM automatically provides credentials or session initiation. This eliminates the need for users to know or store sensitive passwords, while ensuring sessions are monitored, time-bound, and isolated to prevent credential theft or misuse.
- Revoke: Once the task ends, access is revoked, and credentials may be rotated. This step ensures privileged accounts are never left active beyond their purpose, reducing risks of lingering access, insider misuse, or unauthorized reentry.
- Audit: Activities are logged, recorded, and available for compliance or investigation. Every privileged session is tracked in detail, creating an audit trail that supports regulatory requirements, detects anomalies, and strengthens overall accountability within the organization.
This closed-loop process ensures that privileged access is temporary, monitored, and fully auditable.
Why Securing Privileged Access Matters: 4 Perspectives
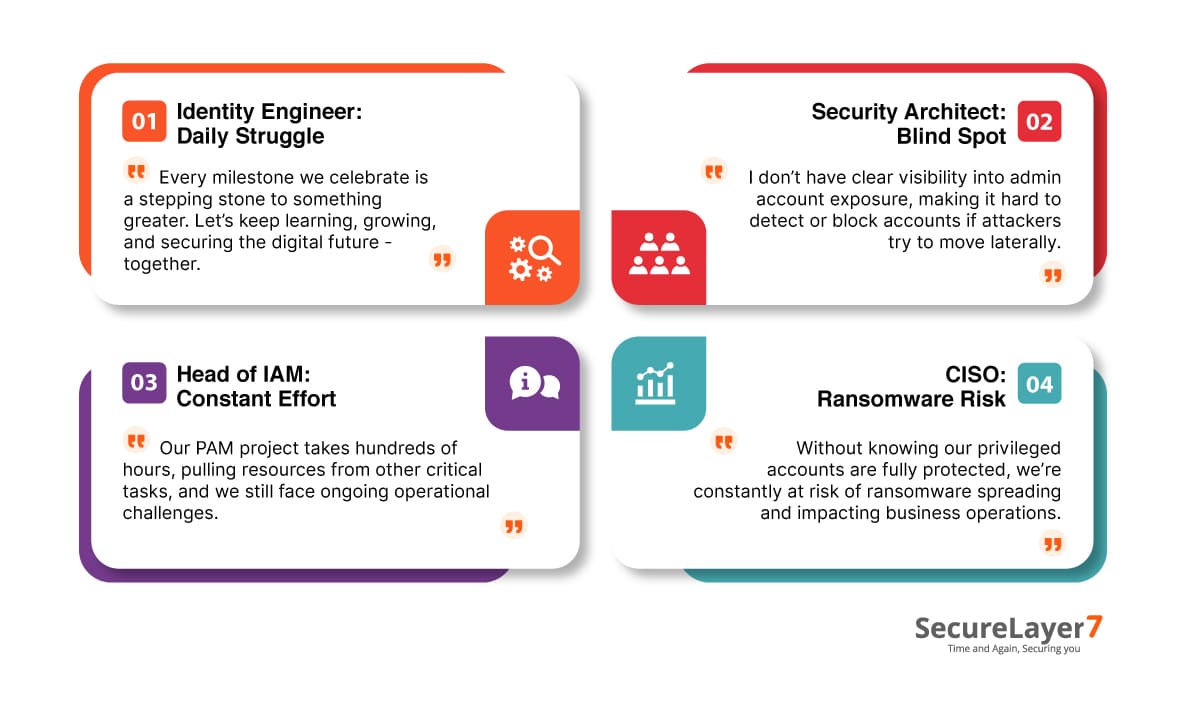
Securing privileged access is crucial for the following reasons:
- CISO: Privileged accounts carry big risk. PAM protects them, reduces insider threats, and ensures compliance.
- IAM Leader: Identity programs often struggle with privilege creep. PAM simplifies control, enforces least privilege, and integrates smoothly with IAM.
- Security Architect: Unseen admin access is a hidden weakness. PAM closes that gap. It delivers just-in-time access, integrates with detection tools, and strengthens resilience by reducing attack surfaces across the enterprise.
- IAM Specialist: Day-to-day identity management is complex. PAM makes privilege handling manageable, automates provisioning, and ensures accountability.
How Does PAM Work?
PAM solutions create robust controls around privileged credentials and the session:
- Secure credential storage: acquires and stores privileged credentials. It isolates common credentials from users. This reduces the chance of password theft, credential sharing, or accidental disclosure.
- Access control: enforces strict access policies to ensure only verified users can reach privileged accounts. These systems often combine multifactor authentication (MFA), adaptive access rules, and role-based controls to align permissions with business needs.
- Just-in-time access: applies a just-in-time access model. Users must submit requests for elevated privileges, which are granted for a limited duration after approval.
- Centralized credential management: centralizes all privileged credentials, such as passwords, SSH keys, and API tokens within a secure vault. This eliminates local storage risks.
- Task automation: automates repetitive administrative workflows, reducing reliance on manual intervention. Automated tasks may include rotating privileged passwords, provisioning and deprovisioning user accounts.
- Session monitoring and reporting: continuously monitors and records privileged sessions, capturing keystrokes, commands, and system changes. These detailed logs help detect suspicious behavior in real time and provide forensic evidence for investigations.
Common Attack Vectors
Here is a list of some common attack vectors used by hackers to exploit privileged access management:
- Credential Exploitation: Attackers steal privileged account credentials through phishing, brute-force attacks, or password spraying.
- Kernel Exploits: Exploiting vulnerabilities in the operating system kernel to run malicious code with system-level privileges.
- Software Vulnerability Exploitation: Hackers use unpatched buffer overflows, memory corruption, or flawed application logic to override security protections and escalate privileges.
- Process Injection/Abuse: Malicious code is injected into privileged processes via DLL hijacking to execute unauthorized actions.
- Misconfiguration Abuse: Exploiting poorly configured permissions, exposed admin interfaces, unnecessary sudo rights, or open network ports.
- Social Engineering: Manipulating users to reveal credentials, approve MFA prompts, or run authorized tools with elevated privileges.
- Pass-the-Hash Attacks: Access password hashes or Kerberos tickets from memory to authenticate as privileged users without needing plaintext passwords.
- Session Hijacking: Taking over active sessions of privileged users to execute commands or access sensitive data at elevated privileges.
- Physical Access Attacks: Gaining direct access to hardware or modifying system files (e.g., Windows “Sticky Keys”) to bypass authentication and escalate privileges.
Real World Examples of Privileged Access Management
Data breaches associated with Privilege access management are common. Below, we have presented two real-world examples to explain the risk:
Example# 1: Snowflake Data Breach
In 2024, Snowflake experienced a massive cloud data breach. The group ShinyHunters exploited privileged accounts to steal massive volumes of sensitive information.
The incident was caused because of weak security controls. Old stolen credentials were never rotated. Network access was open to connections from anywhere. Hackers exploited the gaps in privileged access management.
The fallout of the breach was severe:
- AT&T lost billions of call records.
- Healthcare providers saw 190 million patient records exposed.
- Change Healthcare paid millions in ransom and endured weeks of downtime.
The incident could have been easily avoided by enforcing multi-factor authentication, rotating credentials, and applying just-in-time privileges.
Example # 2: Dropbox Sign Service Account Breach
Dropbox Sign occurred in April 2024. Attackers gain unauthorized access to privileged service accounts.
The compromise gave attackers direct reach into customer databases. They pulled email addresses, usernames, hashed passwords, API keys, OAuth tokens, and even multi-factor authentication data.
The breach forced Dropbox to reset passwords, revoke tokens, and disrupt service for customers worldwide.
The core issue was unchecked privilege for non-human accounts. Proper service account governance and privilege reduction could have helped. Adding behavioral monitoring, just-in-time elevation, and strict API key management might have prevented the incident.
Best Practices in Privileged Access Management
Now that you have gained sufficient understanding of privilege access management framework; let’s explore some best practices to implement in PAMs:
Identify and Inventory All Privileged Accounts
- Map every account that has higher-than-normal permissions across your systems.
- Maintain a list of administrator, service, and application accounts for better visibility.
- Uncover and remove unused, forgotten, or unnoticed accounts that attackers could exploit.
Apply the Principle of Least Privilege
- Users should only have the minimum access required to complete their work.
- Provide elevated privileges only for the duration needed, then revoke them automatically to reduce lingering risks.
Centralize credential and access management
- Use a single platform to handle provisioning and deprovisioning of accounts.
- Apply and enforce access policies consistently across the organization.
- Simplify management while reducing the risk of errors or gaps in control.
Regularly Rotate and Update Privileged Passwords
- Rotate privileged passwords, API keys, and SSH keys automatically to prevent long-term misuse.
- Replace static or forgotten credentials to block attackers from exploiting old access.
- Use a centralized system to enforce rotation schedules and track updates for all accounts.
Enforce Multi-Factor Authentication
- Require MFA (e.g., OTP, authenticator apps, hardware tokens) before granting access.
- Combine passwords with a second factor to stop attackers even if credentials are stolen.
- Enforce MFA across all privileged accounts consistently to ensure full coverage.
Continuously Monitor and Audit Activity
- Review logs and account activity in real-time to detect unusual behavior promptly.
- Set alerts for suspicious actions like privilege escalation or unusual login locations.
- Maintain audit trails to investigate incidents and strengthen compliance posture.
Adopt Just-In-Time (JIT) Access
- Allow elevated permissions only when needed for a specific task, and remove them immediately.
- Limit the time accounts to reduce the attack surface.
Monitor and Record All Privileged Sessions
- Keep track of all privileged sessions in real-time to spot unusual activity.
- Use AI or automated tools to detect abnormal behavior, such as unexpected logins or privilege changes.
- Record sessions for audits and investigations, providing evidence and insights if an incident occurs.
Conduct Regular Audits of Privileged Activity
- Review access logs, session records, and permissions frequently to make sure accounts are used properly.
- Identify unnecessary or excessive privileges to prevent misuse or accidental damage.
- Audits ensure compliance, accountability, and visibility across all privileged accounts.
Enforce Role-Based and Attribute-Based Access Control
Fine-grained control helps reduce risk, simplify management, and keep policies consistent.
- Assign permissions based on job roles, attributes, and context to ensure users get only what they need.
- Adjust access dynamically as roles or responsibilities change to prevent leftover privileges.
Segregate Duties and Disallow Shared Admin Accounts
- Divide responsibilities among multiple users so no single person can perform all critical actions alone.
- Avoid shared admin accounts to ensure every action can be traced to an individual.
- Segregation reduces insider risk and ensures multiple approvals are needed for sensitive tasks.
Integrate PAM with Threat Intelligence and Risk Analytics
- Use AI and analytics to monitor privileged accounts and detect potential threats proactively.
- Assign risk scores to accounts to prioritize high-risk activities and prevent attacks.
- Keep PAM policies updated using intelligence from emerging threats to stay ahead of attackers.
Integrate PAM with Broader Identity and Access Management
Integration improves governance, simplifies management, and strengthens overall security posture.
- Align PAM with the organization’s IAM (Identity Access Management) systems for consistent control of accounts and roles.
- Share account and permission data across systems to close gaps and prevent overlaps.
Implement Zero -Trust Principles
- Verify every access request continuously, regardless of where it comes from.
- Assume breaches can happen and limit what users can access, even with valid credentials.
- Segment privileges and monitor actions in real-time. ckers from moving laterally.
Conclusion
Privileged Access Management is the cornerstone of modern cybersecurity. Unchecked privileged accounts remain a primary vector for attackers, but with proper controls, organizations can reduce risk dramatically.
Organizations that invest in PAM not only protect critical assets but also strengthen compliance readiness. The key is to treat PAM as an ongoing program rather than a one-time deployment. Continuous improvement and user education are critical for long-term success. Ignoring PAMs can put systems at risk. Our experts at SecureLayer7 can help deal with the risk. Contact us now to learn more.
Frequently Asked Questions (FAQs)
Privileged Access Management (PAM) secures and monitors accounts with elevated rights. It is important because these accounts are prime targets for attackers. PAM reduces risk by enforcing control, visibility, and accountability.
IAM manages general user identities and access. PAM focuses on privileged accounts with elevated control over critical systems. While IAM provides authentication and authorization, PAM adds vaulting, monitoring, and auditing tailored for high-risk accounts.
Yes. Regulations like PCI DSS, HIPAA, and SOX require strict control over privileged accounts. PAM helps organizations meet these compliance requirements by providing evidence of monitoring, access control, and auditability.
In cloud environments, PAM secures access to management consoles, API keys, and ephemeral workloads. It enforces just-in-time privileges and integrates with cloud-native IAM services to control and monitor elevated access.
Challenges include user resistance, integration with legacy systems, and deployment complexity. These can be mitigated through phased rollouts, proper training, and selecting flexible PAM platforms.
Start by identifying all accounts across systems. Limit privileged access only to those absolutely necessary, whether human or machine, to minimize risk and reduce potential attack surfaces.
Use role-based or just-in-time access. Provide the least amount of privilege required for a task, enforce time-bound access, and regularly review rights to prevent privilege creep or misuse.
Audit regularly for inactive, outdated, or abandoned accounts. Disable them immediately to close security gaps and reduce opportunities for attackers to exploit forgotten credentials or leftover permissions.
Record, monitor, and analyze privileged sessions in real time. Use alerts, logs, and periodic audits to identify suspicious activity, ensure compliance, and strengthen overall accountability within the organization.



