Whenever you think of mobile app security, the first things that come to mind are firewalls, passwords, multi-factor authentication, and encrypted data. But there is a relatively lesser-known risk: insufficient binary protection, which, if ignored, can be misused by threat actors. This is also the root cause of mobile app repackaging risk.
This OWASP mobile app security risk can leave your app’s business-critical data at the mercy of hackers. According to the BSA’s Global Software Piracy Study, app and game cloning costs over $46 billion annually, with unprotected binaries being a major entry point.
In this blog, we will explore binary security risks, their causes, attack vectors, example scenarios, and best practices to prevent insufficient binary protection.
Understanding Lack of Binary Protection Risks
App binaries are the final packaged version of an application’s source code that runs on a device. Since the binary executes on devices like mobiles or tablets, protecting it becomes crucial.App binaries have emerged as a critical security concern for security teams and that’s why OWASP has put this at the seventh spot in the list of Top 10 Mobile App Security Risk, 2024.
Learn more about detailed list of OWASP Top 10 mobile app security risk, 2024
These binaries may contain critical secrets, such as commercial API keys or hardcoded cryptographic data. Malicious actors can misuse them if they gain access.
Because these binaries often embed sensitive business logic or pre-trained AI models, attackers can exploit them to discover vulnerabilities and launch attacks.
Using this information, attackers can:
- Manipulate app binaries to unlock paid features for free. By modifying the binary code, attackers can bypass in-app purchase mechanisms and unlock premium functionalities without paying legitimate fees.
- Inject malicious code through third-party app stores. Repackaged binaries can be distributed on unofficial stores, exposing users to spyware, trojans, or ransomware disguised as trusted applications.
For example, an attacker modifies app payment identifiers like merchant IDs or wallet addresses to redirect funds. They repackage and distribute this tampered app. Unsuspecting users download it, and payments are diverted to the attacker’s account instead of the intended recipient.
Causes of Insufficient Binary Protection Risks
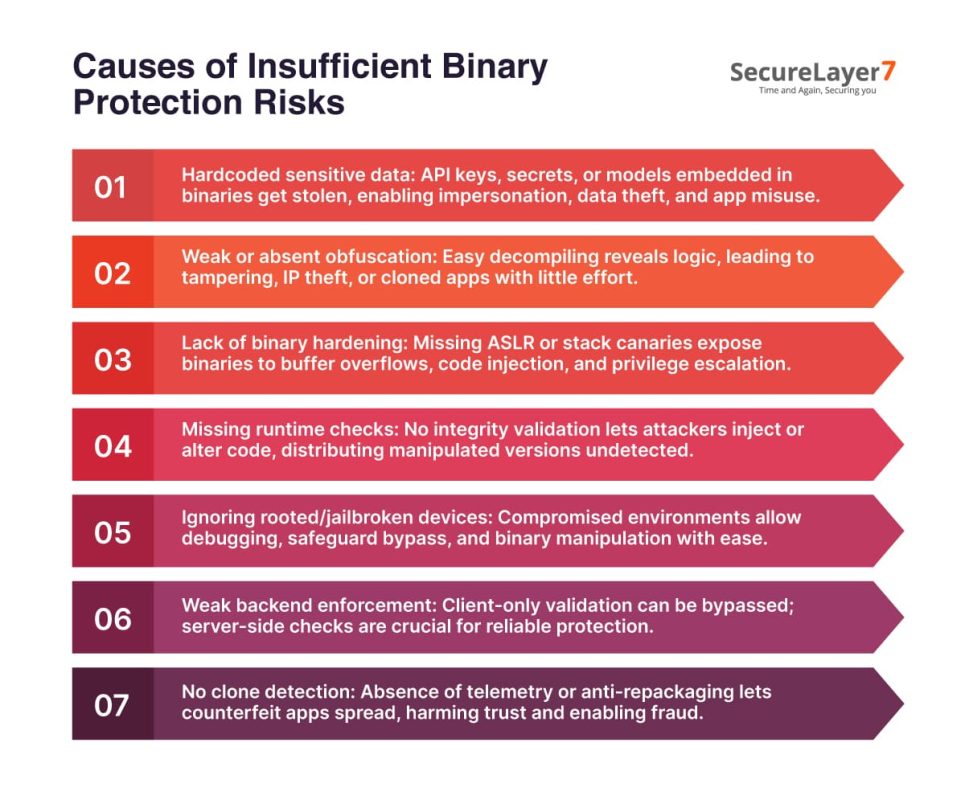
Several technical oversights create opportunities for attackers. From careless coding practices to weak defenses, each misstep leaves binaries vulnerable to reverse engineering, tampering, or malicious redistribution.
- Hardcoded sensitive data or algorithms: Embedding API keys, cryptographic secrets, or proprietary AI models in binaries leaves apps open to theft. Hackers can impersonate apps, access sensitive data, and cause severe risks.
- Weak or absent code obfuscation: Without obfuscation, attackers can decompile or disassemble apps easily. This exposes app logic, enabling tampering, theft of intellectual property, or creation of cloned versions with minimal effort.
- Lack of binary hardening: Failure to implement binary hardening techniques like ASLR or stack canaries allows attackers to exploit vulnerabilities such as buffer overflows, opening doors for code injection or privilege escalation.
- Missing runtime integrity checks: Without integrity checks, apps cannot detect injected or modified code. This gives attackers freedom to alter core functionality or distribute manipulated binaries without detection.
- Inadequate detection of rooted/jailbroken devices: Ignoring rooted or jailbroken device detection enables attackers to exploit weak OS-level protections. They can attach debuggers, bypass safeguards, and manipulate binaries more easily in compromised environments.
- Insufficient backend enforcement of security checks: If validation remains solely on the client side, attackers can bypass it with ease. Backend-based security checks are essential for consistent enforcement and prevention of manipulations.
- No mechanisms to detect unauthorized clones: Without telemetry, anti-repackaging signatures, or clone detection, counterfeit versions spread unchecked. These clones can damage trust, mislead users, and enable fraud at scale.
Security Risks and Business Impact
The consequences of insufficient binary protection extend beyond technical concerns. They directly affect business continuity, customer trust, and even legal compliance. Let’s look at the risks in detail.
- Reverse engineering: Attackers can decompile the app, exposing proprietary algorithms, authentication mechanisms, and hidden functions, all of which can be exploited to bypass protections or replicate sensitive logic.
- Data theft: Poor binary protection can allow unauthorized access to sensitive user data, API keys, and embedded credentials, leading to large-scale breaches and exploitation of private information.
- Code tampering: Attackers may modify an app’s binary to bypass authentication, inject malicious modules, or disable safeguards, ultimately enabling fraud or malware distribution without detection.
- Repackaging and redistribution: Cloned versions with malicious modifications may be published, tricking users into downloading them while undermining trust in the original developer’s brand and application.
- Bypassing security controls: Attackers may disable SSL pinning, jailbreak detection, or purchase restrictions, undermining built-in protections and exposing both businesses and users to unmitigated threats.
Business Impact
- Intellectual property loss: Competitors or hackers may steal proprietary algorithms, features, or designs embedded in binaries, reducing your competitive edge and damaging years of innovation.
- Reputation damage: Customers lose trust quickly when they discover your app is insecure, which can discourage downloads and reduce user engagement across platforms.
- Financial loss: Piracy, app cloning, and fraud from tampered binaries reduce revenue streams while increasing operational costs for fixes, all of which weaken profitability.
- Legal and compliance issues: Insecure apps that lead to breaches may violate GDPR, HIPAA, or other regulations, resulting in lawsuits, penalties, and increased regulatory scrutiny.
- Increased operational costs: Responding to breaches requires additional patching, monitoring, and user support, straining resources and slowing down development pipelines.
Common Attack Vectors
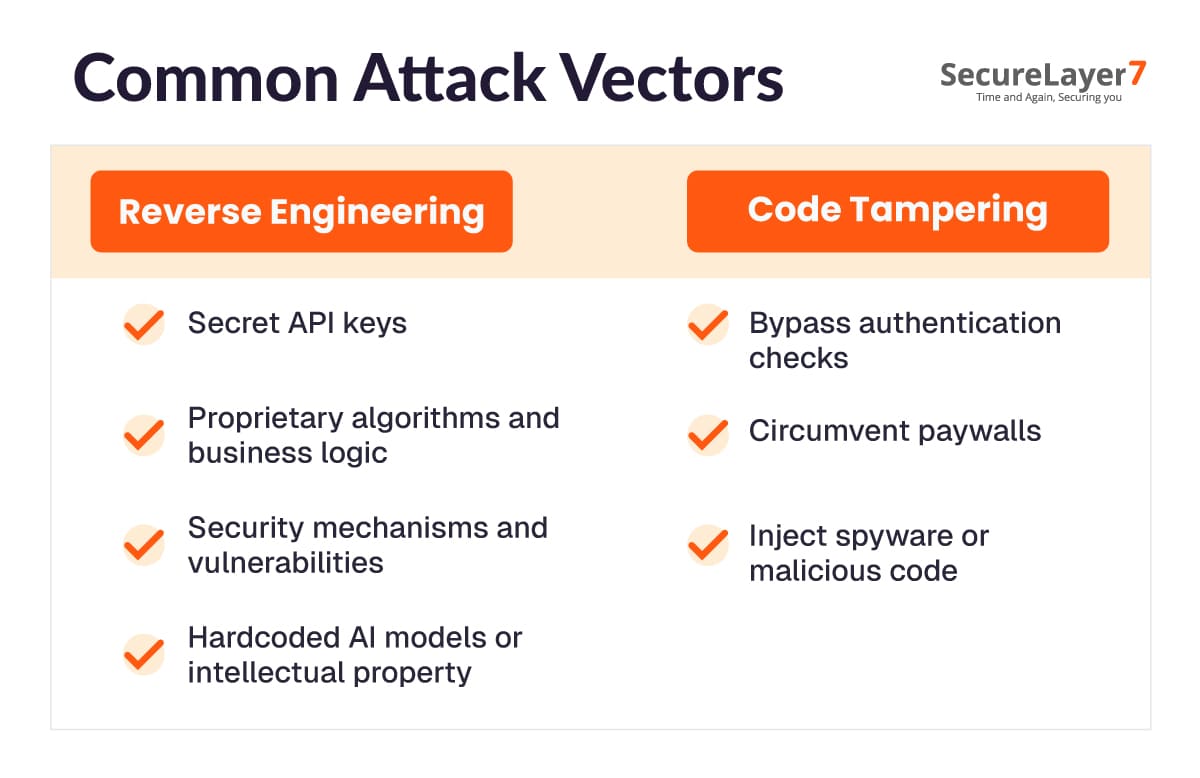
Attackers exploit binaries using common methods. By reverse engineering or tampering, they gain insight into application logic, extract secrets, and alter functionalities to suit malicious objectives.
Reverse Engineering
Through decompiling or disassembling, attackers uncover internal mechanisms. They gain access to:
- Secret API keys: These can be misused to impersonate apps, access third-party services, or abuse paid APIs at the expense of legitimate developers.
- Proprietary algorithms and business logic: Competitors or criminals can replicate unique logic, undermining competitive advantage and devaluing your intellectual property.
- Security mechanisms and vulnerabilities: Attackers analyze exposed mechanisms, identifying weak spots for targeted exploits and bypassing existing protections with precision.
- Hardcoded AI models or intellectual property: Pre-trained models can be stolen, resold, or misused, erasing innovation benefits and reducing return on investment.
Code Tampering
Once attackers understand binaries, they change app behavior to:
- Bypass authentication checks: Unauthorized access to premium features or protected data becomes possible, directly affecting revenue and user trust.
- Circumvent paywalls: Attackers disable payment validations, allowing full access to paid content or features, bypassing legitimate monetization models entirely.
- Inject spyware or malicious code: Binaries are modified with malware to steal sensitive data, track users, or gain deeper access to device-level controls.
Example Attack Scenarios
Real-world examples highlight the severity of insufficient binary protection. These scenarios show how attackers have exploited unprotected binaries for profit, cheating, and intellectual property theft.
Scenario # 1: Exposed API Keys Can Cost a Fortune
If hardcoded API keys are found in binaries, attackers can exploit paid services without authorization. This results in spiraling bills, service disruption, and loss of control.
Scenario # 2: Skipping the Paywall in Games
Attackers reverse-engineered Pokémon Go binaries in 2016, creating clones that allowed cheating and bypassed purchases. Millions downloaded these unofficial apps, damaging revenues and eroding fair gameplay.
Scenario 3: Valuable Features Left Unprotected
If custom features are embedded in binaries without protection, attackers can copy and resell them. This undermines innovation, causes revenue losses, and erodes competitive differentiation.
Real World Incidents
Several high-profile mobile app repackaging incidents have taken place owing to Insufficient binary protection vulnerabilities in the mobile applications. Here is a list of two incidents:
Incident #1 SharkBot Banking
The most recent documented incident involving Insufficient binary protection occurred in March 2025, when a mobile Android banking app was found infected with the SharkBot banking Trojan after being repackaged and distributed through unofficial channels.
Attackers decompiled the legitimate app, embedded the malware, recompiled it, and redistributed the malicious version, enabling credential theft and financial fraud.
Incident # 2 Mamont Attack
In the year 2024, Russian hackers used a new distribution methodology to target Android users using phishing messages that offered products at highly discounted prices.
Victims fell into trap and downloaded a fake shipment tracking app, which, once installed, initiated SMS and USSD-based fraud to steal funds. The campaign saw a massive increase in activity, with Mamont accounting for 36.7% of all mobile banking Trojan attacks.
Best Practices For Prevention
Protecting binaries requires multiple layers of defense. No single control is enough, but together they can significantly reduce exposure to tampering, reverse engineering, and cloning.
Assess Critical Content and Popularity
Protecting binaries starts with knowing which parts matter most. Not every asset is equal, so prioritize based on sensitivity, business value, and exposure.
- Catalog sensitive assets such as API keys, cryptographic secrets, licensing logic, and proprietary algorithms, ensuring they are flagged as top-priority for stronger binary protection.
- Prioritize high-traffic apps with large user bases or those enabling critical business processes, since attackers often target them for maximum disruption or financial gain.
- Evaluate strategic value by identifying apps tied to intellectual property, competitive advantage, or regulatory compliance, ensuring protection efforts focus where compromise would be most damaging.
Use Obfuscation
Obfuscation complicates reverse engineering by hiding code logic. While not foolproof, it raises the cost of attacks and discourages casual tampering attempts.
- Apply proven tools like ProGuard, DexGuard, or iXGuard to obscure code paths, method names, and strings, making binary analysis significantly more time-consuming for attackers.
- Combine layers of obfuscation including string encryption, control flow randomization, and class renaming, ensuring attackers must overcome multiple barriers before extracting useful insights.
- Maintain regular updates to obfuscation patterns, preventing attackers from building reusable deobfuscation scripts that weaken long-term security effectiveness.
Backend Enforcement of Security Checks
Moving critical checks to the backend ensures that attackers cannot simply bypass them by tampering with the client binary.
- Shift sensitive logic such as license validation, payment verification, and access control to backend servers where attackers have no direct modification ability.
- Use attestation mechanisms like SafetyNet or Apple DeviceCheck to verify device integrity before granting backend access, blocking compromised or emulated environments.
- Implement certificate pinning to prevent attackers from intercepting traffic with forged certificates, ensuring client-server communications remain trustworthy and tamper-resistant.
Runtime Integrity and Tamper Detection
Applications must protect themselves at runtime, detecting manipulation attempts and responding quickly to prevent further compromise.
- Deploy RASP solutions that monitor runtime behavior, spotting suspicious activity such as method hooking, code injection, or debugger attachments in real time.
- Verify digital signatures of binaries during execution, ensuring that no unauthorized modifications or repackaged versions are running in production environments.
- Integrate integrity checks for critical libraries and configuration files, triggering alerts or shutting down when unauthorized changes are detected.
Least Privilege Principle
Excessive permissions create unnecessary attack surfaces. By limiting access, you reduce the potential damage if binaries are compromised.
- Request only essential permissions during app design, avoiding unnecessary access to device sensors, storage, or communications channels attackers could exploit.
- Restrict sensitive APIs by enforcing strict access controls, ensuring only authorized processes or roles can invoke high-risk operations.
- Use role-based controls to segment privileges, limiting the blast radius of compromise to only what is strictly necessary for a user’s role.
Detection of Rooted/Jailbroken Devices
Attackers often exploit rooted or jailbroken devices to bypass security controls. Detecting such environments reduces the risk of tampering.
- Perform filesystem checks for telltale signs of rooting, like presence of su binaries, system partition modifications, or unauthorized package managers.
- Use behavioral analysis to detect suspicious activity such as privilege escalation attempts, unauthorized API usage, or abnormal system calls.
- Restrict features or block app functionality when devices are compromised, ensuring attackers cannot exploit weakened environments for deeper attacks.
Ongoing Monitoring and Response
Security does not end at release. Continuous monitoring helps spot attacks early and prepare quick responses.
- Track cloned versions in unofficial app stores, taking action to remove them before they spread to users and damage brand trust.
- Monitor API traffic for anomalies like sudden spikes, unauthorized calls, or unusual geolocation patterns indicating potential tampering or automation.
- Maintain incident response playbooks specifically for binary threats, ensuring your team can act quickly when tampering or repackaging attempts are detected.
Accept the Arms Race
Binary protection is never absolute. Security teams must accept the ongoing battle and continuously raise the bar against attackers.
- Combine layered defenses like obfuscation, runtime protection, monitoring, and backend enforcement to make attacks costlier and less rewarding for adversaries.
- Update protections regularly to keep pace with evolving attacker techniques, avoiding reliance on outdated defense methods.
- Conduct penetration testing to identify weaknesses in binary protections, ensuring your defenses remain strong against modern attack tactics.
Closing Thoughts
Binary attacks are inevitable in today’s application-driven world. Preventing insufficient binary protection requires layered defense, obfuscation, binary hardening, secure API communication, and ongoing monitoring. Organizations must consider app’s binaries as a crucial security concern as it allows hackers to tamper and reverse-engineer mobile apps, causing significant security risk for users and businesses.
At SecureLayer7, our experts can help safeguard your app binaries and protect your business-critical assets. Contact us today to discuss your security needs.
FAQs on Insufficient Binary Protection
Frequent unauthorized access, reverse-engineered app code, or increased support cases from cloned apps are indicators of binary risks and a lack of protective mechanisms.
They reverse engineer binaries to extract data, identify vulnerabilities, or inject malicious code. Modified apps are distributed widely, bypassing security and tricking users.
Insufficient protection leads to intellectual property theft, reputational harm, revenue loss, legal penalties, and reduced customer trust. It can also cause fraud, service disruption, and compliance failures.



