In 2025, NightSpire ransomware emerged as one of the most serious cybersecurity risks because of its notoriously ruthless double extortion tactics. It targets sectors and industries vital to our everyday lives, such as healthcare, manufacturing, IT services, and public infrastructure.
With reported attacks spanning continents, such as North America, Europe, Asia, and the Middle East, the fast spread has been alarming. One of the most striking incidents occurred at Al Tadawi hospital in the UAE, where patients’ including PIIs, payment details, and medical history related data was compromised. This incident serves as a sobering reminder of the severe impact of the threat.
At the heart of NightSpire’s extortion model is their dark web leak site. This group escalates the pressure on victims by displaying countdown timers alongside the stolen data, forcing organizations to make hasty decisions under duress.
In this blog, we’ll explore in detail about NightSpire Ransomware, how it works, threat profile, Indicators of Compromise, and how to defend against it.
What is NightSpire Ransomware?
NightSpire ransomware refers to a security threat which first steals sensitive data from an organization and then encrypts that data, holding it hostage until the victim pays a hefty ransom.
And if their demands are not met, victims face the horrifying prospect of having their private data leaked publicly, placing immense pressure on them to comply.
This approach has solidified NightSpire’s reputation as a major player in the dark web, and as a group to be feared. These attacks are considered more serious as they combine stealth, persistence, and psychological intimidation.
In a very short span, NightSpire ransomware has made its mark because of its capability to enter the most sophisticated networks and systems.
NightSpire’s Dark Web Infrastructure
NightSpire’s dark web infrastructure serves as the backbone of its extortion model. The group maintains a dedicated leak site that lists breached organizations and exposes stolen files. Countdown timers display how long victims have before their data is made public.
Communication is conducted through encrypted channels like ProtonMail and Telegram, helping them stay anonymous and avoid law enforcement tracking.This well-structured ecosystem makes NightSpire particularly hard to disrupt. For defenders, monitoring their leak portals and communication footprints can provide early warning indicators of ongoing campaigns.
Target Profile and Notable Victims
NightSpire picks targets the way a predator picks ground—where a strike will hurt the most. Healthcare, education, manufacturing, retail and IT services sit high on its list because outages and data loss there cause real-world chaos.
The group isn’t picky about geography and they operate across the U.S., UAE, Europe and Asia. The breach of a UAE hospital, roughly 1.5 TB of data taken, is an example of their appetite for data-heavy victims that can’t afford long interruptions.
Their entry methods are painfully familiar: weak VPNs, misconfigured firewalls and unpatched systems. Those holes let them slip in, move laterally and grab whatever looks valuable.
How NightSpire Works
Every ransomware operation follows a specific process. Each phase builds on the last, moving from quiet reconnaissance to full-scale disruption and ransom. Here’s how the attack unfolds:
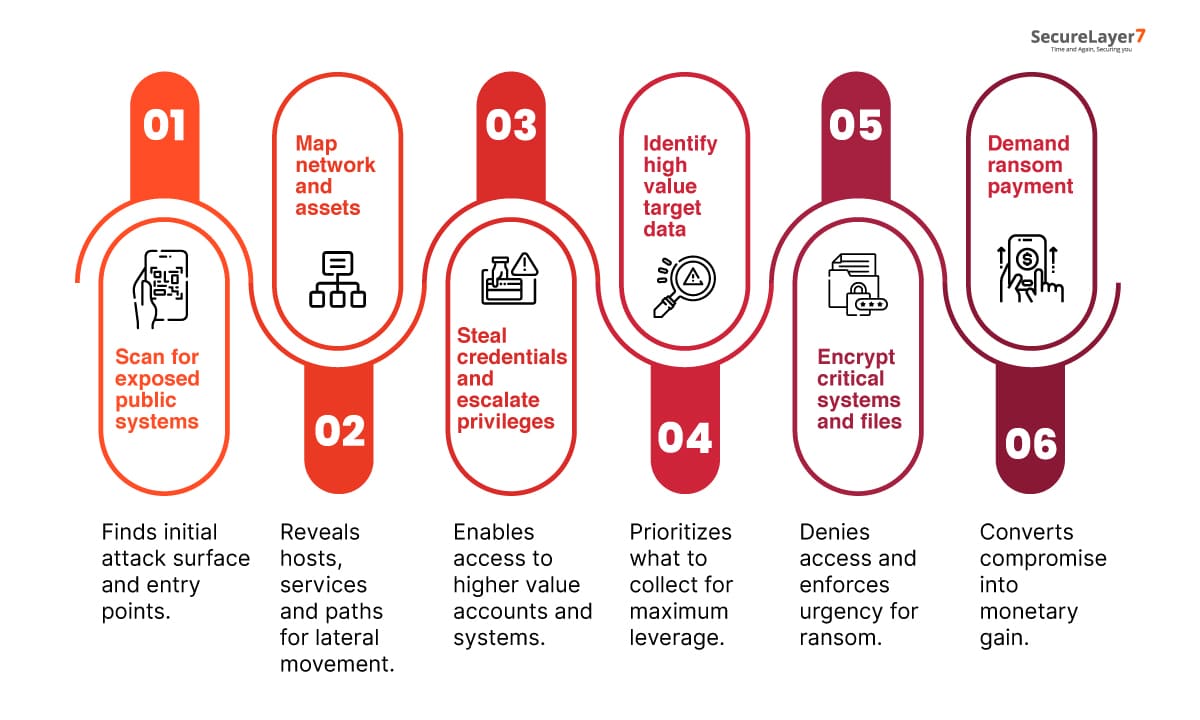
- Phase 1: Scanning for Exposed Systems: NightSpire begins by scanning the internet for vulnerable systems, such as servers with open ports, outdated software, or weak passwords. This stage helps attackers map their first foothold into the organization’s network.
- Phase 2: Mapping the Network: Once inside, they quietly explore. The attackers identify hosts, services, and internal connections, creating a blueprint of how data and devices interact. Every discovered system becomes a potential route for lateral movement.
- Phase 3: Stealing Credentials and Escalating Privileges: Next comes identity theft. NightSpire steals employee credentials through phishing or malware, then uses them to access administrator-level accounts. With these privileges, attackers gain control over sensitive systems and security policies.
- Phase 4: Identifying High-Value Data: With control established, they search for what matters most—financial records, confidential projects, customer databases, or executive communications. This data becomes the leverage they’ll use when ransom demands begin.
- Phase 5: Encrypting Critical Systems: When the groundwork is complete, NightSpire locks everything down. Files and servers are encrypted, backups are often destroyed, and operations grind to a halt. This creates panic and urgency inside the organization.
- Phase 6: Demanding the Ransom: Finally, the ransom note appears. Attackers demand payment—usually in cryptocurrency, promising decryption keys or silence in return. Some even threaten to publish stolen data if the organization refuses to pay.
NightSpire’s process shows how cyberattacks today aren’t random, they’re systematic, patient, and deeply strategic. Each phase is designed to weaken defenses and maximize leverage before striking the final blow.
NightSpire Attack Methods and Techniques
NightSpire uses a mix of planned steps and known weaknesses to break in:
- They often exploit known vulnerabilities. A key example is CVE-2024-55591 in FortiOS, which can let attackers bypass authentication. Because FortiOS is common in enterprises, that flaw gave NightSpire wide access in early 2025.
- After gaining access, they use legitimate admin tools, such as PowerShell, MEGACmd, WinSCP, and Everything.exe to move through networks quietly. Using normal tools helps them look like routine activity and avoid easy detection.
- They rely on “living off the land binaries” (LOLBins). This means using trusted system tools to run commands and move data, which reduces alerts from signature-based security tools.
Their methods show technical skill and an understanding of enterprise defenses. The group also uses censorship-resistant, encrypted channels for operations, while publicly shaming victims on their leak site.
NightSpire’s evasion and pressure techniques make detection and response difficult. They combine encryption with public leaks and time pressure to force victims into paying quickly.
Real World Case Study of NightSpire Ransomware Attack: Encryption in Action
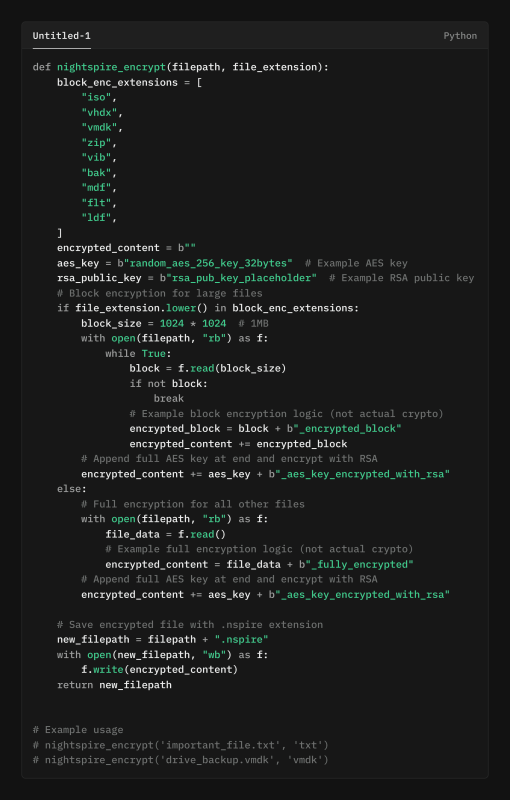
The technical sophistication of NightSpire rests in its flexible encryption strategy. The malware identifies specific file extensions, such as ISO, VHDX, VMDK, ZIP, VIB, BAK, MDF, FLT, and LDF that are typically associated with large storage or backup files, applying block encryption in 1MB increments. NightSpire moves fast and with intent. It doesn’t scroll slowly through folders. Once it finds the important stuff, NightSpire locks it down, leaving core system folders isolated so the machine still looks “alive.”
You’ll find the clue in the filenames: encrypted files end with .nspire. That tiny marker tells you what happened, even if the rest of the system seems normal.NightSpire stays quiet on purpose so everything looks normal while it works that delays detection and buys the attackers time.
Behind the scenes, every file is locked with its own secret code, and those codes are themselves locked with a master key only the attackers have. In short, each file needs the criminals’ key to be opened again.
They also don’t bother wiping backup shadow copies. That’s not kindness, it’s about moving fast. Skipping that step lets them cause maximum disruption before anyone can respond.
CVE-2024-55591: The Primary Attack Vector
One clear example is CVE-2024-55591 in FortiOS; that flaw lets remote actors bypass authentication and walk straight into protected networks. NightSpire leaned on this vulnerability during its early 2025 campaigns, and for good reason, it opened doors that would otherwise be locked.
FortiOS firewalls are everywhere: enterprises, government agencies, and service providers. That ubiquity gives attackers broad reach. When a gateway device sitting on the internet has a hole like this, many networks suddenly become easy marks.
Why this vector worked so well boils down to three simple fact:
- Widespread deployment. FortiOS runs across diverse organizations, so a single exploit scales.
- Public exposure. Firewalls are meant to face the internet, which makes them visible targets for remote scanning and exploitation.
- High impact. An authentication bypass hands an attacker privileged access immediately — no credential theft or lengthy pivoting required.
Taken together, these factors turned CVE-2024-55591 from a technical footnote into a practical shortcut for fast, damaging intrusions.
NightSpire Indicators of Compromise (IOCs)
Security teams should monitor for the following indicators of compromise (IOCs) associated with NightSpire ransomware:
- Creation of “.nspire” and “readme.txt” files in sensitive directories
- Unusual execution of legitimate tools (WinSCP, MEGACmd, PowerShell, Everything.exe)
- Rapid, large-scale file encryption
- Encrypted or missing backups
- Spikes in outbound traffic or unauthorized access attempt
How to Prevent NightSpire Attack
NightSpire ransomware poses a significant threat to organizations, leveraging advanced techniques to infiltrate and encrypt critical systems.
- Deploy EDR solutions to identify unauthorized tool use and file encryption behavior, ensuring real-time detection and rapid response to suspicious activities across endpoints.
- Review system logs and conduct proactive threat hunting to uncover hidden threats, leveraging expert analysis and advanced analytics for early breach detection.
- Monitor for LOLBins and proxy execution activity, using behavioral analytics to spot misuse of legitimate tools for malicious purposes.
- Patch all public-facing systems, especially VPNs and firewalls, to close vulnerabilities and reduce attack surface for ransomware exploitation.
- Enforce multi-factor authentication (MFA) and least-privilege access, minimizing the risk of credential compromise and limiting lateral movement.
- Deploy endpoint detection and response (EDR) solutions for real-time visibility, enabling continuous monitoring and immediate action against threats.
- Segment networks to restrict lateral movement, isolating critical assets and containing potential breaches within defined zones.
- Maintain offline, immutable backups and test recovery processes regularly, ensuring data resilience and rapid restoration after an attack.
- Develop and test incident response playbooks tailored for ransomware events, ensuring preparedness and coordinated action during real incidents.
By adopting a zero-trust security model and conducting regular vulnerability assessments, organizations can minimize exposure and improve resilience against evolving threats like NightSpire.
Conclusion
NightSpire ransomware exemplifies how modern cybercriminals blend stealth, extortion, and psychological pressure. Their rapid evolution and cross-sector targeting make them a serious global threat.
Organizations must act decisively through timely patching, strong access controls, network segmentation, and continuous monitoring. Backups should be secure, offline, and regularly tested. A well-prepared incident response plan can mean the difference between swift recovery and catastrophic loss.
Staying informed, alert, and proactive remains the best defense against NightSpire and the next wave of ransomware threats.
Dealing with NightSpire requires specialized expertise. Connect with the SecureLayer7 team today to assess your organization’s security posture and implement a proactive protection strategy that keeps your critical assets secure.
Frequently Asked Questions (FAQs)
NightSpire is a financially motivated ransomware group that emerged in 2025, known for double extortion tactics and high-value global targets.
They exploit vulnerabilities in public-facing systems, use legitimate tools for lateral movement, and threaten data leaks after encryption.
Healthcare, manufacturing, retail, IT services, education, and public sector entities are among the top targets.
Look for “.nspire” file extensions, abnormal PowerShell or WinSCP activity, and rapid file encryption events.
Regular patching, MFA enforcement, network segmentation, offline backups, and employee awareness training.
Isolate affected systems, engage an incident response team, and seek legal counsel before considering ransom payment.



