The threat landscape has drastically changed in the last decade, and so does the threat perception. Organizations now prefer a shift-left approach, instead of reacting to an incident. Cyber kill chain is a robust step in this direction.
The Cyber Kill Chain framework for computer network defense is not a platform that can be integrated into enterprise defenses. But it can be applied to mitigate cyber threats and build resilience.
In this blog, we’ll dive deeper to understand the cyber kill chain framework, how it works, and best practices for implementation.
What is a Cyber Kill Chain?
The cyber security kill chain framework helps security teams, investigators, and malware analysts understand how attacks unfold. It shows each step an attacker takes, how they enter in the system, and how they move. Cyber kill chain enables defenders to prepare better defenses.
This matters because attacks today are sophisticated. They are more complex, more destructive, and harder to stop. Hackers often use many different attack paths at the same time. This multiplies the damage and makes life harder for response teams.
Cyber kill chain was developed by Lockheed Martin, which is a step-by-step method used to spot and stop enemy actions. The model maps out the key stages of a cyberattack and highlights the points where security teams can block, detect, or disrupt attackers.
These attacks often use a mix of malware, ransomware, trojans, spoofing, and social engineering to reach their goal.
Why It Matters
Cyber kill chain is a foundational framework that serves various purposes:
- CISOs use them for strategic security investments, risk management, and regulatory compliance. They can identify critical vulnerabilities, resource allocation, and evaluate the effectiveness of security controls.
- SOC (Security Operations Center) managers use cyber kill chain to structure detection, analysis, and response workflows. The model provides a repeatable, stage-by-stage process for triaging incidents, carrying out root cause analysis, and deploying limiting measures.
- Security analysts and threat hunters use the cyber kill chain to understand attacker tactics, techniques, and procedures (TTPs). It helps them correlate alerts, prioritize investigations, and identify patterns in complex attack scenarios.
How Cyber Kill Chain Works: Step-by-Step Process
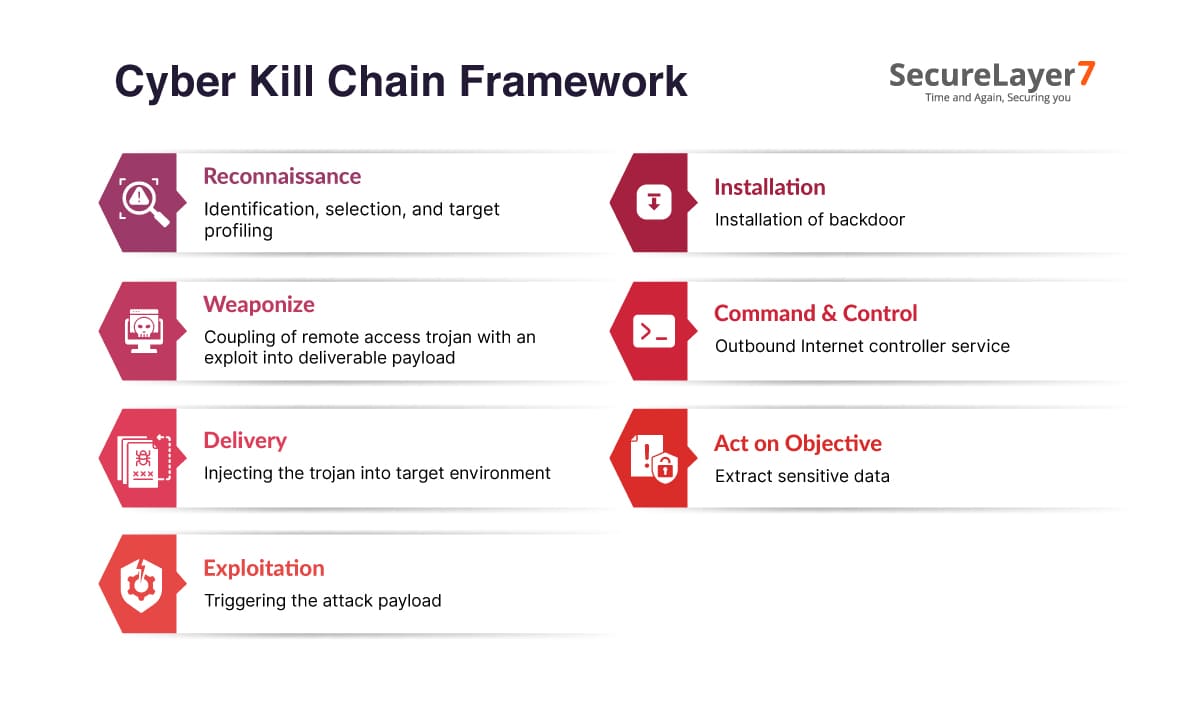
Here is the step-by-step process of cyber kill chain mechanism:
1. Reconnaissance
Reconnaissance is the process of gathering information about the potential target. This can be an individual or an organizational entity. Reconnaissance helps attacker to make decisions about the type of weapon suitable for the target, which type of delivery methods is required for malware installation difficulties, or what kind of security mechanisms need to be bypassed.
Reconnaissance can further be broken down to three parts:
- Target identification
- Selection
- Profiling
Reconnaissance includes crawling websites, blogs, social relationships, mailing lists and network tracing tools to get information about the target. This information is further used to design and deliver the payload.
Reconnaissance is divided into two types:
- Passive : This step is carried out without letting the target know about it.
- Active : This step involves much deeper profiling that may trigger an alert to the target.
2. Weaponize
In the next stage, attackers design and build a payload using a Remote Access Trojan (RAT). They try different delivery methods, such as phishing emails, malicious attachments, or compromised websites to penetrate defenses.
Mostly, they prefer custom or zero-day exploits as they are difficult to detect. The purpose is to create a stealthy, effective payload that hits the target.
3. Delivery
The payload is now pushed into the target environment through email attachments, infected USB drives, compromised web pages, or supply-chain channels. Advanced attackers may stage watering-hole attacks or poison software updates. When users or systems execute the malicious content, the objective is achieved. .
4. Exploitation
Once the payload is triggered, it exploits a vulnerability to execute arbitrary code and gain initial access. The vulnerability can be anything like a software flaw, a misconfigured service, or simply weak credentials. The exploit grants elevated privileges or a foothold inside internal networks.
5. Installation
After gaining a foothold, attackers install persistent backdoors or implants to keep access. They deploy rootkits, trojans, or custom agents and take steps to evade detection.
6. Command & Control
Compromised systems create channels through encrypted connections to external servers, peer-to-peer relays, or traffic hidden in legitimate cloud services. Attackers use domain generation to obscure command signals to send instructions, fetch tools, and coordinate lateral movement.
7. Act on Objective
Now, attackers exfiltrate sensitive data, deploy ransomware, steal credentials, or disrupt services, causing data loss, financial damage, regulatory exposure, and reputational impact.
Disrupting the Cyber Kill Chain: Proactive Strategies for a Stronger Defense
The threat landscape is evolving, yet the methods attackers use to reach their objectives remain surprisingly familiar. This is where the cyber kill chain proves valuable. It gives defenders a lens to understand how threats unfold.
To protect an organization, defenders must proactively disrupt each stage of the chain and make the environment far harder for attackers to succeed.
1. Adopt Shift-Left Approach
A robust security starts before the threat appears. A shift-left approach ensures security is woven into processes during the early stage. Think of security as a critical ingredient, not a garnish over the food plate.
Here is how you can do it:
- Add Static Application Security Testing (SAST) to your CI/CD pipeline to catch vulnerabilities before they ever make it to production.
You can achieve this by using a SIEM or Threat Intelligence Platform to connect unusual events such as odd login patterns, large transfers, or traffic to known malicious IPs.
- Regular testing closes the loop. Penetration tests and audits uncover cracks that might otherwise widen into entry points.
Conduct annual penetration tests on web applications to expose flaws like SQL injection or cross-site scripting, then remediate quickly or deploy controls such as web application firewalls.
2. Build a Multi-Layered Fortress
No single defense can hold forever. It eventually breaks. Multilayered ensures that if one safeguard fails, others remain to stop the breach. But this is not limited to using firewalls and antivirus.
It’s about creating layers of protections across networks, endpoints, applications, and data, all reinforced by an educated workforce.
- Network segmentation limits lateral movement inside the environment.
- Endpoint Detection and Response (EDR) tools monitor continuously for suspicious activity and enable swift containment.
- Least Privilege Access narrows the attack surface by restricting users to only what they need.
3. Break the Kill Chain
The power of the cyber kill chain lies in its detail. Each stage can be disrupted with specific defenses.
- Reconnaissance is about protecting your digital footprint.
Monitor public sources for sensitive exposure, remove it quickly, and use domain privacy to hide WHOIS data.
- Weaponization, Delivery, and Exploitation demand blocking malicious payloads.
Enforce application whitelisting, apply patches quickly, and secure high-value assets with multi-factor authentication.
- Command & Control (C2) focuses on persistence and attacker communication.
Implement EDR (Endpoint Detection & Response) for deep monitoring and rely on network segmentation to limit the damage of a compromise.
- Actions on Objectives are about protecting data and systems from theft or disruption.
Apply Data Loss Prevention (DLP), enforce encryption in transit and at rest, and maintain immutable, offsite backups.
4. Strengthen the First Line
Technology alone can’t hold the line. Employees are the first line of defense and their awareness can make a difference.
Provide mandatory, continuous training on phishing, social engineering, password hygiene, and data privacy. Reinforce with simulated phishing campaigns to build practical awareness.
Cyber Kill Chain vs. MITRE ATT&CK
Two of the most influential frameworks in cybersecurity, Cyber Kill Chain and MITRE ATT&CK, serve complimentary but distinct roles in this arena.
Cyber Kill Chain breaks down cyberattacks into a linear sequence of seven stages, from initial reconnaissance to achieving the attacker’s objective. It’s designed to help organizations visualize and disrupt attacks by focusing on key prevention points along a defined attack path.
MITRE ATT&CK, on the other hand, is a dynamic, matrix-based framework that catalogs hundreds of real-world adversary tactics and techniques. Instead of a fixed sequence, ATT&CK maps the many ways attackers move through systems, persist, and evade detection, enabling detailed threat hunting, forensic analysis, and detection engineering.
Get a deeper understanding of the MITRE ATT&CK framework.
While the cyber kill chain is ideal for strategic defense planning and incident response, MITRE ATT&CK provides the granularity needed to detect, investigate, and mitigate complex, multi-vector attacks, including those that do not follow a predictable order.
Many mature security programs now use both frameworks together: Kill Chain for high-level attack modeling and ATT&CK for in-depth adversary emulation and detection.
Conclusion
The cyber kill chain is not merely an academic framework; it’s a tactical guide. By embedding security early, building layers of defense, disrupting each stage, organizations can shift the balance of power in their favor.
Security is not a destination but an ongoing practice. The more proactive the mindset, the stronger the defense. Contact us today to learn more about how to build cyber resilience.
FAQs
The framework highlights each step attackers take, allowing teams to spot early warning signs, prioritize response, and stop intrusions before they cause real damage.
Using email filters, endpoint detection, network segmentation, strong authentication, and real-time monitoring helps disrupt attackers at every step and reduce their chances of success.
Its step-by-step approach often overlooks cloud risks, insider misuse, and API abuse. Attackers rarely follow fixed patterns, which leaves blind spots if used alone.
It connects threat intelligence with daily monitoring and response, helping teams predict attacker moves, respond faster, and reinforce defenses with practical, context-driven insights.



