Every digital activity, whether sending an email, participating in a video call, or making an online purchase, involves the movement of data from one system to another. This process follows a complex and structured path defined by the OSI Model, or Open Systems Interconnection Model. Though not a new concept, the OSI Model has long been fundamental to modern networking.
In the fields of cybersecurity and network engineering, the OSI Model serves as a practical tool for diagnosing problems, designing secure systems, and comprehending potential vulnerabilities. From threat detection to packet analysis, it provides essential insights into how data flows securely across digital environments.
What is the OSI Model?
The OSI Model defines how data is transmitted between devices through a series of pre-established checkpoints, known as layers. Each layer of this model performs a specific function, allowing professionals to troubleshoot, secure, and optimize networks with greater effectiveness.
Developed by the International Organization for Standardization (ISO) in the 1980s, the OSI Model was created to bring order to the early chaotic days of networking. At that time, different companies utilized their own protocols, leading to compatibility issues across systems and devices. The OSI framework introduced a universal reference model and established a common language for network communication.
Why the OSI Model Matters
Nowadays, the TCP/IP model is more prevalent in Internet architecture and that’s why some security experts tend to believe the OSI Model. But that’s a mistaken notion. Even though modern networking relies on TCP/IP, the OSI model is widely used as a conceptual guide to visualize and diagnose data movement and understand and observe invisible network behavior.
Understanding OSI layers helps in:
- Designing scalable systems by clearly defining the function of each layer, such as which layer handles encryption, routing, or error correction.
- Focusing on one layer at a time engineers to pinpoint issues like packet loss, latency, or link misconfigurations.
- Analyzing network security cybersecurity as attackers operate at different OSI layers. It helps to understand whether a denial-of-service may hit Layer 3 or 4, while SQL injections can strike at Layer 6.
- Planning for incident response as during breach teams can trace data flow through layers to isolate where compromise occurred.
OSI model’s relevance has all the more increased with the advent of hybrid clouds, IoT networks, and Zero-Trust architectures. It serves as a universal blueprint by bringing clarity to chaos, and facilitating in-depth understanding of shared networks.
The Seven Layers of the OSI Model
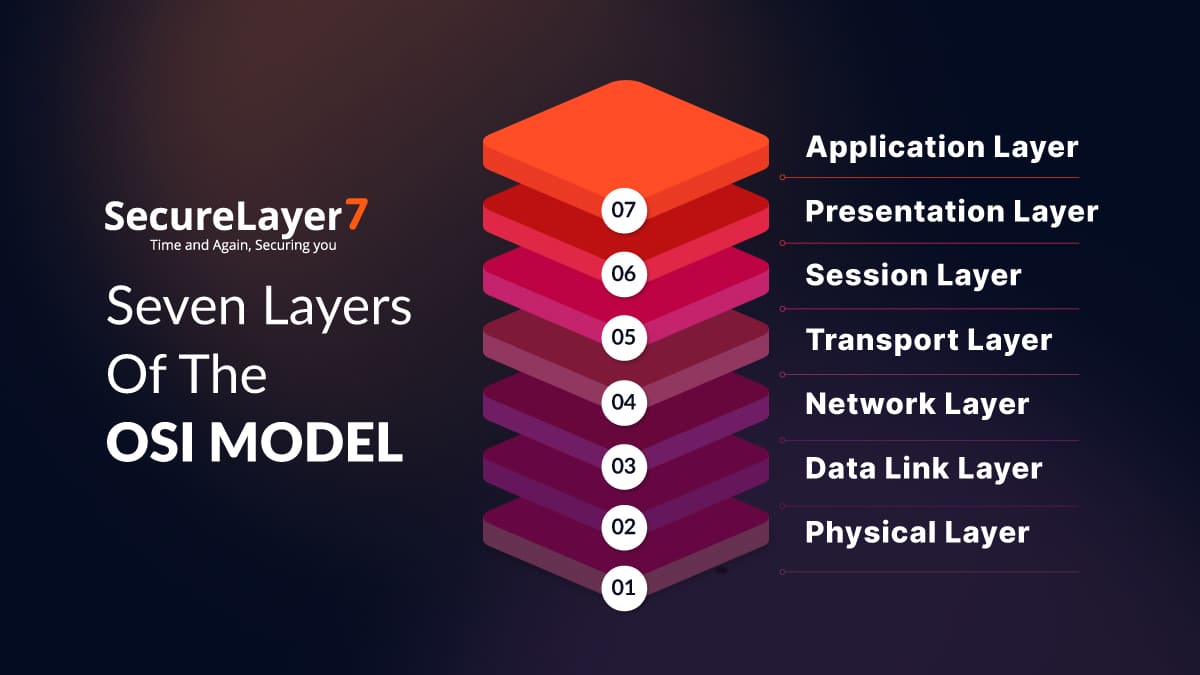
There are seven layers in the OSI stack and each layer performs a distinct role while data moves from one device to another. Below we have explained each of these seven layers in detail.
Layer1: Physical Layer
The physical layer is the backbone of the OSI model and this is responsible for transmitting raw binary data that may include electrical, optical, or radio signals caring bits (0s and 1s).
Physical layer has the following components:
- Cables containing Ethernet, fiber optics, or coaxial
- Connectors, switches, hubs, and network interface cards (NICs)
- Voltage levels, signal timing, and data rates
This layer is responsible whenever physical breaks happen. For example, a loose cable, bent fiber, or electromagnetic interference can cut off communication completely.
Put simply, the physical layer acts as an electrical, mechanical, and procedural interface for a medium of transmission.
The physical layer defines the following:
- the shapes and properties of the electrical connectors
- the frequencies to transmit on
- the line code to use
- various low-level parameters
A common example is when an Ethernet cable is unplugged, it can disconnect a user’s connection despite software configurations being correct. Attackers can exploit this vulnerability using signal jamming or hardware tampering.
Key fact: Sniffing attack is the most common attack on the physical layer of the OSI stack. Attackers can read data packets using sniffer packets if data is unencrypted.
Layer 2: Data Link Layer
Once raw bits are transmitted, the data link layer ensures they are organized into frames and transmitted error-free between directly connected devices. This is the protocol layer responsible for transferring data moving between nodes on a network segment.
The purpose of this layer is to provide a functional and procedural means to transfer data between network components. Also, this is the layer where errors related to the physical layer are corrected.
Ethernet, IEEE 802.11 WiFi protocols, ATM and Frame Relay are popular examples of the data link layer. This is the most complex layer of the OSI stack.
The key function of the data link layer includes:
- Encapsulation of network layer data packets
- Breaking data into frames for transmission
- Identifying physical device addresses on the network
- Ensuring reliable delivery using checksums or CRC
- Regulating data pace between sender and receiver
- Facilitates the operation of switches by using MAC addresses.
Sublayers of data link layer include:
The data link layer is further divided into two sub-layers, which are as follows:
- Logical Link Control (LLC) deals with multiplexing, which involves the flow of data among applications and other services. It provides error messages and acknowledgments as well.
- Media Access Control (MAC) manages the device’s interaction and controls physical media access. It gets the information in the form of packets from the Network layer, divides packets into frames, and forward it bit-by-bit to the physical layer.
However, despite utility, data link layer has limitations, such as:
- Can operate only within LAN ( Local Area Network)
- Increases the overhead by adding header, trailer, and redundant data.
- Error handling dependency is largely in the upper layer.
- Cannot handle end-to-end communication.
- Lacks routing decision making capability
- Consumes extra processing power
Layer 3: Network Layer
Understanding the Network Layer is crucial for anyone diving into the world of networking. This layer takes charge of how data packets travel across various interconnected networks, ensuring they reach their intended destination seamlessly. Common Protocols: TCP, UDP, SCTP
Unlike the Data Link Layer, it can manage end-to-end communication and can be scaled up easily.
Key functions of the network layer include:
- Assigning IP addresses (IPv4, IPv6) to devices, ensuring accurate identification and communication across networks.
- Encapsulates transport layer segments into packets to ensure smooth transmission.
- Ensures packet delivery from the input interface of a router to desired output interface at a defined IP destination.
- Helps in choosing the most efficient routes using dynamic protocols like OSPF, BGP, or RIP.
- Fragmenting packets for efficient delivery
- Handling congestion and network path optimization
A popular example is a router inspects the destination IP in each packet and forwards it toward the appropriate next hop. In cybersecurity, IP spoofing or route hijacking often occur at this layer. Attackers manipulate routing tables or use fake IPs to divert traffic. Network segmentation and secure routing protocols help minimize risk.
Layer 4: Transport Layer
Layer 4 simplifies things by providing standardized access to essential services such as reliable connections, flow control, and multiplexing.
This means that higher application layers, such as layer 5 to 7 don’t have to worry about the specifics of the communication network. One of its key tasks is end-to-end error recovery, which enhances data reliability.
Layer 4 is especially good at load balancing because it can make fast routing decisions without needing to look into the content of messages. It uses straightforward methods like round-robin routing, making it efficient for packet-level management.
For more complex needs, such as routing based on media type or application, layer 7 load balancing comes into play, allowing for detailed traffic analysis.
This layer ensures end-to-end communication between hosts is reliable and properly sequenced. It breaks large chunks of data into smaller segments and reassembles them upon arrival.
Core functions include:
- Reliable delivery (TCP) or fast transmission (UDP)
- Error recovery, retransmissions, and congestion control
- Managing sessions between applications
- Port addressing for process-to-process communication
A popular example is when you use online banking, TCP establishes a handshake to ensure every data packet reaches intact. In contrast, video streaming apps often use UDP for lower latency, tolerating minor packet loss.
Attacks like SYN floods target this layer by overwhelming servers with half-open connections. Firewalls and rate-limiting systems protect against such abuse.
Layer 5: Session Layer
The session layer facilitates the establishment, management, and termination of sessions between end-user application processes, creating a semi-permanent dialogue. Common protocols include NetBIOS, PPTP, RPC
These communication sessions involve a series of requests and responses exchanged between applications. Session-layer services are particularly valuable in environments utilizing remote procedure calls (RPCs).
A notable example of a session-layer protocol is the OSI protocol suite’s session-layer protocol, referred to as X.225 or ISO 8327. This protocol is capable of attempting to recover connections in the event of a loss.
If a connection remains inactive for an extended period, the session-layer protocol may close and subsequently reopen it. It supports both full-duplex and half-duplex operations and incorporates synchronization points within the stream of exchanged messages.
Additional implementations of the session layer include the Zone Information Protocol (ZIP), which manages name binding in the AppleTalk protocol, and the Session Control Protocol (SCP), utilized in the DECnet Phase IV session-layer protocol.
Within the OSI network architecture, the session layer responds to service requests from the presentation layer and generates service requests to the transport layer.
These functions include the following:
- Setting up and maintaining session states
- Handling session termination and recovery after failure
- Managing authentication and authorization
A common example is during a remote desktop session, this layer ensures the connection remains active. If a network drop occurs, the session can be restored without restarting.
From a security lens, session hijacking is a critical risk at this level. Attackers steal session tokens to impersonate users. Using secure cookies, session timeouts, and TLS encryption reduces such exposure.
Layer 6: Presentation Layer
This layer acts as a translator for data. It formats and converts data between the application layer and network. It also handles encryption, compression, and data encoding.
Key responsibilities include the following:
- Data format translation (text, image, video)
- Encryption and decryption for confidentiality
- Data compression for faster transmission
A common example is when you access a secure website, your browser decrypts HTTPS traffic at this layer using SSL/TLS protocols. It transforms unreadable ciphertext into human-readable content. Cyberattacks like SSL downgrade attacks exploit this layer, forcing weaker encryption methods. Modern TLS enforcement and HSTS policies safeguard against such downgrades.
Common protocols of presentation layer include: SSL, TLS, JPEG, MPEG, ASCII
Layer 7: Application Layer
Layer 7, also known as the application layer, is the topmost level of the OSI Model, which consists of seven layers in total. It facilitates data processing just beneath the surface of the software applications that users engage with. For instance, HTTP requests and responses that load webpages are classified as layer 7 events.
DDoS attacks targeting this layer are referred to as layer 7 attacks or application layer attacks.
It’s important to note that DDoS attacks can also occur at layers 3 and 4 of the OSI Model, highlighting the range at which these security threats can manifest.
Key functions of the application layer include:
- Enabling communication between software and the network
- Handling user authentication and input validation
- Managing data formatting for user interfaces
Common Protocols in the application layer include the following: .
- HTTP protocol used in web communication (Port 80).
- DNS to convert domain names into IP addresses.
- TELNET for remote login and file management.
- DHCP (Dynamic Host Configuration Protocol) to assign IP addresses to hosts dynamically. .
- FTP (File Transfer Protocol) to enable file transfer between systems.
- SMTP (Simple Mail Transfer Protocol) to handle sending of emails.
Let’s try to understand this with an example:
When you send an email through Outlook, the SMTP protocol helps send the message, while DNS translates the website names into IP addresses. Layer 7, which users interact with, often attracts attacks.
Issues like SQL injections, HTTP floods, and DNS poisoning take advantage of flaws in web applications. To reduce these risks, it’s important to validate inputs, use Web Application Firewalls, and conduct regular code reviews.
OSI Model vs TCP/IP Model
While OSI provides the theoretical structure, the TCP/IP Model powers real-world communication. TCP/IP combines some OSI layers into four broader layers: Network Interface, Internet, Transport, and Application.
Here is how both stack up against each other:
- OSI is conceptual; TCP/IP is implementation-based.
- OSI separates Presentation and Session layers; TCP/IP merges them into its Application layer.
- TCP/IP focuses on end-to-end transmission, making it more practical for the Internet.
TCP/IP stack is a critical component of the operating system. It enables network communication, and if ignored, it can be an entry point for hackers.
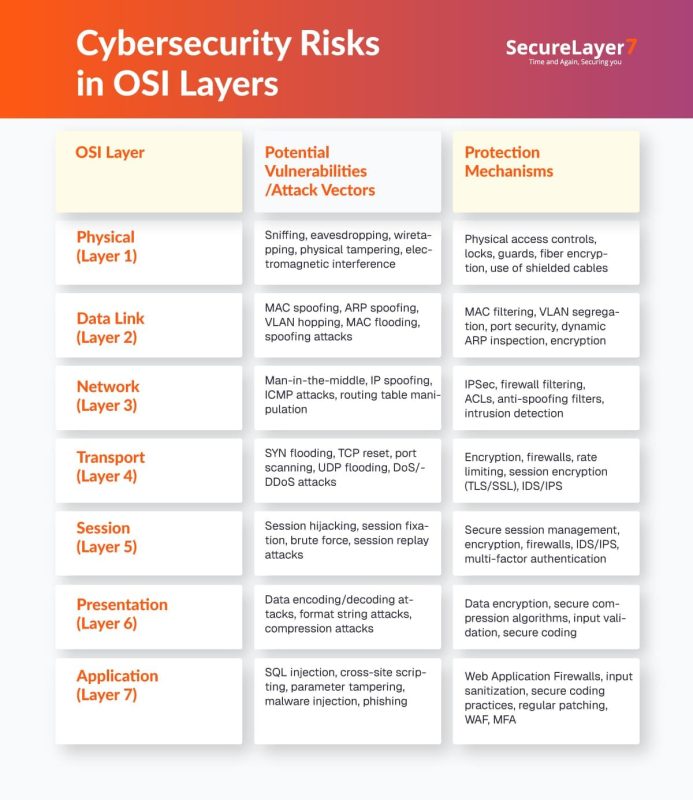
Potential Cybersecurity Risks in Each Layer
Each of the layers of the OSI model poses some risk as outlined in the below infographics:
Conclusion
The OSI Model is more than a theoretical concept—it’s a lens for understanding every digital interaction. By separating complex processes into seven layers, it empowers IT professionals to build, secure, and repair networks methodically.
Whether you’re analyzing cyber threats, optimizing bandwidth, or designing cloud architectures, the OSI Model provides clarity in a world of invisible connections. Mastering it means mastering the language of the internet itself.
Ignoring the security of applications and networks across the OSI stack can be risky. SecureLayer7 can help identify these risks to ensure your system remains safe. Contact us today to learn more to know how we can help.
FAQs About the OSI Model and 7 Layers
The primary goal of the OSI model is to standardize communication and interoperability between different hardware and software systems.
OSI is a conceptual framework; and TCP/IP defines actual internet protocols.
The reason is it’s directly exposed to users and vulnerable web interfaces.
It lets engineers isolate and diagnose problems layer by layer and this helps them figure out the issue on their own.
Yes. It remains a vital learning and troubleshooting framework in cybersecurity and cloud networking.



