Have you ever heard of a backdoor attack? It’s a stealthy method cybercriminals use to gain unauthorized access to digital systems. Unlike traditional methods, such as phishing or brute force attacks, backdoors allow attackers to maintain control without being detected. These hidden openings can linger in systems for months or even years, giving cyber villains ample time to harvest sensitive data or disrupt operations.
Recognizing a backdoor is a real challenge, like trying to find a hidden lockpick in a wall. That’s why understanding the mechanics of these attacks and their various forms is crucial for anyone concerned about cybersecurity.
In this blog, we’ll dive deep into how backdoor attacks work, the signs to look for, and strategies to detect or prevent them. Stay tuned to safeguard your digital life!
What is a Backdoor Attack?
A backdoor attack is a hidden mechanism that allows threat actors to bypass standard authentication or security controls. Developers may intentionally insert backdoors for maintenance or troubleshooting purposes, while attackers may introduce them to gain unauthorized access.
In certain contexts, legitimate backdoors can serve useful functions; for example, system vendors may include them for diagnostic purposes, or governments may require them for lawful interception.
Nonetheless, when these access points are exploited by malicious actors or created by attackers, they become serious threats to security.
Malicious backdoors allow attackers to:
- Steal sensitive information such as intellectual property, customer records, or financial data;
- Perform fraudulent transactions without triggering alerts;
- Install spyware, keyloggers, or Trojans that monitor user activity;
- Launch denial-of-service (DoS) attacks or disrupt operations;
- Hijack servers to host illegal content or mine cryptocurrency;
- Deface websites to damage credibility or spread propaganda.
The real danger with backdoors isn’t just how they enter into the system, but how quietly they work. A lot of advanced persistent threats (APTs), often linked to government-backed groups, rely on these backdoors to operate.
Once they’re in, attackers can move around networks freely, gain more control, and keep accessing systems even if passwords are changed or security is improved. Essentially, a backdoor isn’t just a way in; it’s a lasting grip that changes the dynamics in a digital space.
How Does a Backdoor Attack Work?
At its core, a backdoor attack unfolds in three stages:
- Initial compromise: Attackers breach a system through malware infection, vulnerability exploitation, or insider cooperation.
- Backdoor installation: A hidden mechanism is deployed, often disguised as a legitimate file, driver, or plugin.
- Persistent control: The attacker maintains undetected access, issuing commands or exfiltrating data at will.
This flow is deceptively simple. What makes backdoor attacks insidious is the variety of techniques attackers employ to establish and preserve access.
For example:
- Temporary maintenance hooks:Developers may leave behind debugging or maintenance functions that attackers exploit. It is like a mechanic leaving a spare key under the hood of a car; useful for quick service, but dangerous if discovered by strangers.
- Covert channels:Attackers can send stolen data in disguised forms, such as embedding commands in normal network traffic. The activity blends with everyday noise, making detection harder.
- Kernel-level or application-level backdoors:Rootkits burrow deep into an operating system’s kernel, while application-level backdoors attach to specific programs. Both allow attackers to manipulate processes invisibly.
- Web shells:Lightweight scripts planted on web servers that give attackers remote command execution, often used after exploiting a website vulnerability.
- Malware staging: Backdoors frequently act as launchpads for additional payloads. For instance, a seemingly harmless downloader may later pull in ransomware or spyware.
What begins as a single point of compromise can therefore evolve into a multi-layered, long-term occupation of the system.
Types of Backdoor Attacks
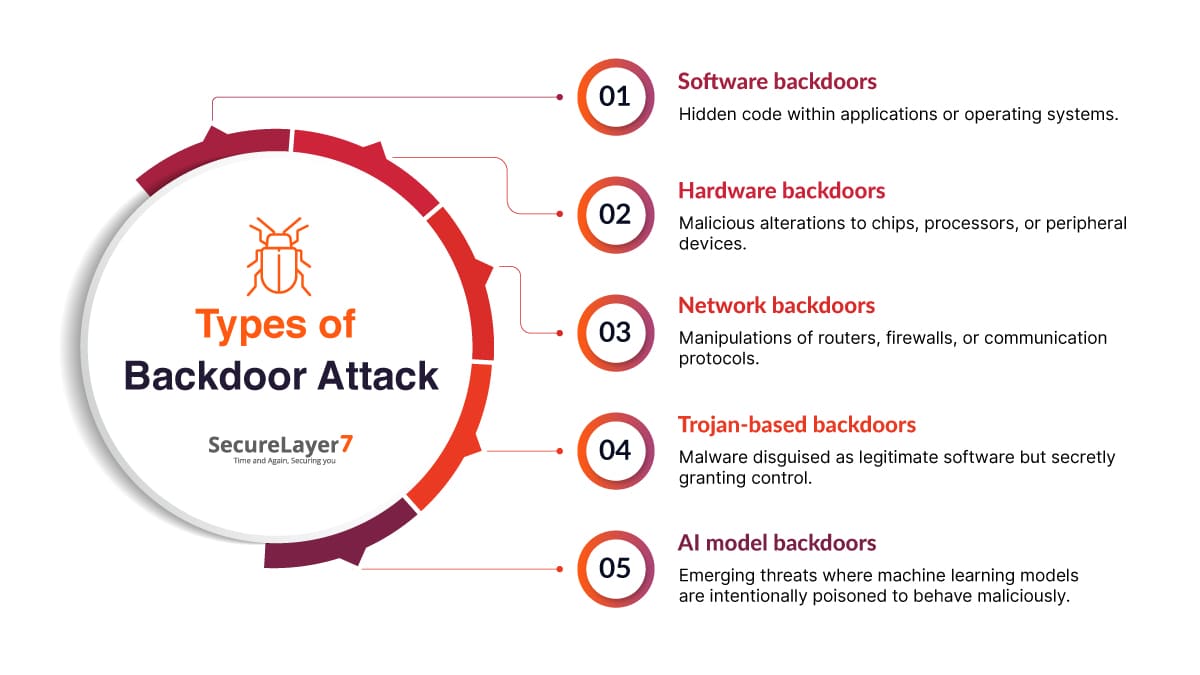
Backdoors come in several forms depending on how they are created and where they reside. Broadly, they can be classified as:
- Hardware backdoors are malicious modifications to chips, processors, or peripherals that enable stealthy control. Verify supply chain provenance, perform hardware attestation, lab testing, and publish validated findings for authoritative remediation.
- Network backdoors manipulate routers, firewalls, or protocols to eavesdrop or persist access. Use continuous monitoring, packet forensics, configuration baselines, and peer-reviewed incident reports to prove compromise and guide authoritative fixes.
- Trojan-based backdoors hide inside legitimate-looking software, then open remote control channels. Confirm via behavioral analytics, reproducible sandbox traces, digital signatures, and published indicators-of-compromise to establish expert confidence and remediation guidance.
- AI model backdoors involve poisoning training data or models to trigger malicious outputs. Detect with adversarial testing, provenance audits, explainability reports, and peer-reviewed validation to maintain trust and accountability practices.
Other Variants of Backdoor Attacks
In many cases, existing malware families double as backdoors. Examples include:
- Cryptojacking tools that hijack processing power for mining cryptocurrency;
- Ransomware that locks files but also installs persistence mechanisms;
- Spyware and keyloggers that collect inputs and system behavior;
- Trojans masquerading as useful apps while opening hidden access points.
These types underscore how flexible the concept of a backdoor is—it can be a line of code, a modified USB stick, or even a corrupted AI dataset.
Common Techniques Used by Attackers
Attackers do not rely on a single trick. Instead, they exploit weak points across software, hardware, and human behavior. Some of the most common techniques include:
- Exploiting unpatched software, weak credentials, or misconfigurations: Old software bugs, default settings, and easy passwords are open doors.
- Phishing and social engineering: Attackers convince users to download malicious files or share credentials.
- Malicious downloads and drive-by infections: Compromised websites or free software bundles often conceal backdoors.
- Supply chain compromises: Inserting backdoors into trusted software updates, as seen in high-profile breaches.
- Island hopping through vendors: Targeting third-party suppliers to indirectly access larger organizations.
- Federated learning poisoning: Manipulating AI training data in distributed environments to embed backdoors.
- Hardware backdoors:Rogue microchips or tampered USB drives that carry hidden instructions.
- IoT exploitation:Devices with default or weak passwords become easy entry points into larger networks.
- Maintenance hooks:Leftover developer tools repurposed as backdoors.
- Covert channels:Hidden data transfers masked in normal traffic.
- Kernel and application backdoors: Deeply embedded or program-specific access routes.
- Web shells:Browser-based command execution for remote attackers.
- Malware staging:Using initial backdoors to download and launch additional payloads.
Each technique represents not just an entry point but also a persistence strategy. Once a foothold is secured, attackers can escalate privileges, move laterally, and quietly expand their influence.
Real-World Examples of Backdoor Attacks
The SolarWinds Orion supply chain attack stands out as one of the most notorious backdoor incidents in recent history. Attackers infiltrated the software build process of SolarWinds, a widely used IT management platform, embedding a malicious backdoor known as SUNBURST into legitimate Orion software updates.
Because these updates were properly signed and trusted, thousands of organizations, including US government agencies, unwittingly downloaded them. By early 2020, the compromised updates had been widely disseminated.
This allowed attackers to gain remote access, conduct reconnaissance, and exfiltrate sensitive data from high-value targets. The operation went undetected for months, utilizing advanced stealth techniques to disguise command-and-control traffic within normal patterns.
The fallout was severe:
- Thousands of customers were potentially exposed.
- The company suffered a huge financial impact.
- Long-term reputational damage across both government and private sectors.
The SolarWinds case illustrates why backdoors are so dangerous: they exploit trust. When trusted software itself becomes the delivery vehicle, even vigilant organizations struggle to defend against compromise.
Risks and Impacts of Backdoor Attacks
The consequences of backdoor attacks vary. In some cases, damage is immediate and visible, such as when attackers deface a website. In other cases, the effect emerges slowly, like an undetected leak that gradually drains resources.
Key risks include:
- Unauthorized access to sensitive data: Attackers can steal trade secrets to customer databases.
- Deployment of additional malware: Such backdoors often pave the way for ransomware, spyware, or botnets.
- Operational sabotage:Attackers can disrupt services, disable systems, or corrupt data.
- Stealthy persistence: These backdoors are like hidden residents in a house; they can observe, manipulate, and control without detection.
- Corporate espionage: Stolen intellectual property can give competitors or adversaries significant advantages.
- National security threats: backdoors in critical infrastructure or defense systems can compromise entire nations.
How to Identify Backdoor Attack
Signs of compromise may include unexplained network traffic, unusual system processes, or unexpected changes in configuration. Still, backdoors are designed to hide, so systematic detection methods are essential.
Common approaches include:
- Anti-malware tools for identifying known backdoor signatures.
- Application and web firewalls to block suspicious requests or unauthorized traffic.
- Intrusion Detection Systems (IDS) and Endpoint Detection and Response (EDR) for monitoring system behavior for anomalies.
- Honeypots decoy systems designed to attract and study attackers.
- Network monitoring for continuous inspection for covert channels or abnormal data flows.
Once detected, removal requires careful forensic investigation. Simply deleting a suspicious file may not be enough; attackers often install multiple redundant access points. Best practices include:
- Isolating affected systems;
- Conducting full forensic analysis to trace the entry point;
- Removing all malicious code and hidden processes;
- Rebuilding or hardening compromised systems;
- Updating security controls to prevent reinfection.
Backdoor removal is not just about cleaning up—it is about ensuring the system cannot be re-compromised through the same pathway.
How to Prevent Backdoor Attacks
The best defense against backdoors is proactive prevention. This involves a layered strategy combining technical controls, human awareness, and organizational processes.
Key measures include:
- Comprehensive reviews help uncover vulnerabilities and misconfigurations before attackers exploit them.
- Remove unused applications, disable unnecessary services, apply timely patches, and enforce strong access controls.
- Combine audits, hardening, monitoring, and threat hunting to create overlapping protections.
- Restrict execution to trusted applications and plugins, reducing unauthorized software risks.
- When maintenance backdoors are necessary, use them temporarily and remove them promptly afterward.
- Equip staff to recognize phishing, suspicious downloads, and social engineering attempts.
Preventive strategies may not eliminate every risk, but they raise the cost and complexity for attackers, making successful backdoor exploitation far less likely.
Conclusion
Backdoor attacks are a really sneaky kind of cyber threat as they often go unnoticed and rely on tricking people into trusting them. These attacks can happen through software weaknesses, hardware tricks, or even through smart devices and manipulated AI. Essentially, backdoors can infiltrate almost any part of our digital lives.
In the world of cybersecurity, the dangers often remain hidden until it’s too late.Our security experts can help proactively discover such attacks Contact us today to learn more.
Frequently Asked Questions (FAQs)
By performing audits, patching vulnerabilities, hardening systems, training employees, and monitoring networks for anomalies.
No. While antivirus can detect known signatures, sophisticated backdoors often evade traditional tools. Layered defenses are necessary.
A trojan backdoor is malware disguised as a legitimate program that installs a hidden access point. Once installed, attackers can remotely control the system, steal data, or download additional payloads. Check processes, digital signatures, and vendor provenance to detect trojans.
A shell backdoor or web shell is a small script on a web server that gives an attacker remote command execution via HTTP. It’s commonly planted via vulnerable uploads or unpatched CMS plugins and should be hunted in writable web directories.
Backdoor websites host or deliver malicious code, act as command-and-control servers, or lure victims into installing backdoors. They can compromise legitimate sites or purpose-built malicious domains; monitor outbound DNS/HTTP patterns to spot them.
Combine allowlisting, file-scanning, EDR behavioral rules, web application firewalls, strict upload controls, patching, and DNS monitoring. Regular supply-chain checks and vendor validation reduce risk from backdoor websites and trojan backdoors.



