Advanced Persistent Threats (APTs) represent some of the most sophisticated and damaging cyberattacks faced by organizations today. Unlike quick, opportunistic hacks, APTs are long-term, targeted intrusions designed to infiltrate networks, stay undetected, and steal valuable data over extended periods. These attacks often involve multiple stages – from gaining initial access through phishing or exploiting vulnerabilities to maintaining persistence and moving laterally within systems – all while evading detection.
Because APTs are often backed by well-funded cybercriminals or nation-state actors, they demand more than basic security defenses. Detecting and mitigating APTs requires advanced threat intelligence, continuous monitoring, and layered security strategies to safeguard your organization’s critical assets.
Evolving Threat Landscape and Sophisticated Attacks
The cybersecurity landscape has evolved rapidly over the past decade, with attackers using advanced techniques such as automation, social engineering, and Zero-Day Attacks to bypass traditional defenses. As organizations expand across cloud platforms, IoT devices, and hybrid infrastructures, the attack surface has grown exponentially – creating more entry points for cybercriminals.
Unlike conventional malware attacks aimed at quick disruption, today’s adversaries pursue long-term, undetected access to critical systems. This shift has given rise to Advanced Persistent Threats (APTs) , a new class of cyberattacks defined by their stealth, precision, and endurance.
Overview of APTs and How They Differ from Typical Cyberattacks
Advanced Persistent Threats (APTs) differ from standard cyberattacks in both scale and intent. While typical attacks often aim for quick data theft or financial gain – such as through ransomware – APTs are carefully orchestrated, long-term campaigns. These attacks are usually carried out by highly skilled groups with significant resources, often linked to organized cybercrime or nation-state actors.
Unlike regular malware infections that are detected and removed within hours or days, APTs can stay hidden for months or even years. They rely on custom-built malware, advanced evasion techniques, and covert command-and-control (C2) channels to continuously extract sensitive data without raising alarms. Their persistence and stealth make them among the most challenging and dangerous threats to detect and contain.
SolarWinds Attack: A Landmark APT Case Study
The SolarWinds supply-chain attack remains one of the most notable examples of an Advanced Persistent Threat (APT) in recent history. By compromising the build environment of SolarWinds’ Orion platform, attackers inserted malicious code into legitimate software updates – giving them covert access to thousands of organizations, including government agencies and Fortune 500 companies.
This incident reshaped how organizations view vendor security, emphasizing the need for supply-chain visibility, integrity validation, and continuous monitoring.
For more insights on this topic, read Supply Chain Attacks: Examples and Preventive Measures, which explains how third-party compromises can propagate through global networks.
What is an Advanced Persistent Threats (APTs)
An Advanced Persistent Threat (APT) is a long-term, targeted cyberattack in which skilled threat actors infiltrate a network to steal sensitive data or secretly monitor activities over an extended period. Unlike quick, opportunistic hacks, APTs are strategic, stealthy, and well-funded, often leveraging custom malware, zero-day exploits, and social engineering to evade detection.
These attacks typically target high-value organizations – such as government agencies, financial institutions, and technology firms – and can maintain unauthorized access for months or even years. The term “advanced” reflects the sophisticated tools and techniques used, “persistent” emphasizes the ongoing, covert nature of the attack, and “threat” points to the deliberate human intent driving it.
Definition of an APT and What Makes It “Advanced” and “Persistent”
An Advanced Persistent Threat (APT) is a highly sophisticated, long-term cyberattack in which an intruder gains unauthorized access to a network and remains undetected for an extended period. The term “advanced” refers to the use of complex techniques – such as zero-day exploits, custom malware, and encrypted command-and-control (C2) channels – that allow attackers to bypass traditional security defenses.
The “persistent” element reflects the attacker’s intent to maintain continuous access to the compromised environment rather than carrying out a single, quick intrusion. This persistence enables them to methodically collect sensitive data, monitor communications, and manipulate systems – all while evading detection by security teams.
How APTs Differ from Conventional Cyberattacks
Unlike typical cyberattacks that aim for immediate disruption or profit (for example, ransomware or phishing scams), APTs are strategic and stealth-driven. Attackers behind APTs carefully plan their operations, selecting specific targets – often government institutions, critical infrastructure, or large enterprises – to achieve espionage or long-term data theft.
Key differentiators include:
- Stealth: APTs use techniques like fileless malware, legitimate administrative tools, and encrypted traffic to avoid detection.
- Persistence: Attackers continuously adapt their methods to retain access, even after partial detection or cleanup.
- Targeting: APTs are not random; they focus on high-value organizations with sensitive intellectual property, financial data, or strategic intelligence.
The Rise of APTs in Modern Cybersecurity
The rise of APTs parallels the global surge in digital connectivity and cyber espionage. As organizations migrate to cloud environments and adopt remote work models, their attack surface has expanded, offering more opportunities for adversaries to exploit. Over the past decade, several nation-state-sponsored groups and cybercriminal syndicates have leveraged APT tactics to infiltrate critical sectors such as defense, finance, healthcare, and energy.
Incidents like Stuxnet, SolarWinds, and APT29 (Cozy Bear) have demonstrated how APTs can disrupt economies, compromise national security, and undermine public trust.
How APT Attacks Unfold
Advanced Persistent Threats (APTs) are not single, quick-hit cyberattacks – they are long-term, highly organized campaigns designed to silently infiltrate and control a network for months or even years. Understanding how APT attacks unfold is key to recognizing, preventing, and mitigating their impact.
Below is a breakdown of the typical APT attack lifecycle, from initial entry to data theft and persistence.
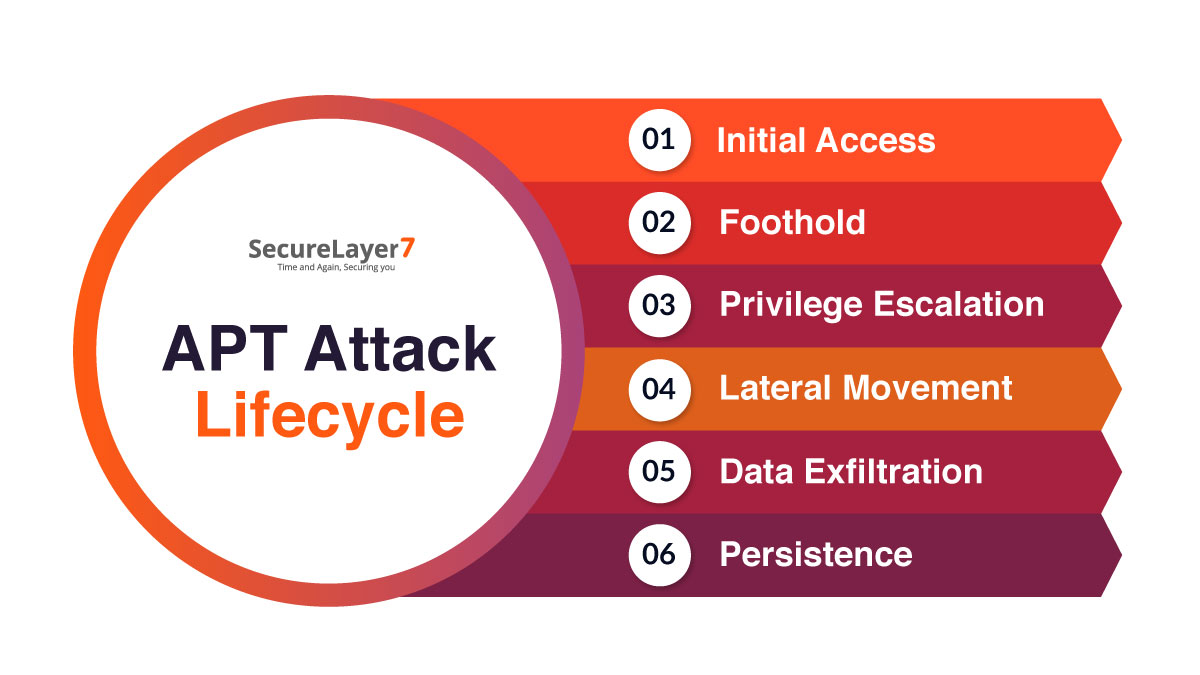
Initial Access: Phishing, Exploiting Vulnerabilities, or Compromised Credentials
Every APT begins with an entry point. Attackers often rely on social engineering or technical exploitation to gain that first foothold.
- Phishing emails remain the most common entry vector, tricking employees into clicking malicious links or downloading infected attachments.
- Exploiting software vulnerabilities in unpatched applications, misconfigured systems, or exposed APIs provides another stealthy entry route.
- Stolen or brute-forced credentials from the dark web or reused passwords can allow attackers to bypass authentication altogether.
Establishing Foothold: Installing Backdoors or Tunnels
After initial access, attackers must ensure they can return undetected. This is done by installing backdoors, remote access trojans (RATs), or command-and-control (C2) tunnels that allow continuous access to the compromised environment.
These footholds enable them to:
- Maintain communication with external servers.
- Re-enter the system even after reboots or software updates.
- Move data and commands in and out of the environment securely.
Escalating Privileges: Gaining Administrative Access
Stable presence established, attackers aim to gain higher privileges. Their objective is to move from a low-level user account to full administrative or domain control.
Common methods include:
- Exploiting privilege escalation vulnerabilities in the OS or applications.
- Harvesting cached credentials using tools like Mimikatz.
- Abusing misconfigured Active Directory permissions or shared drives.
Lateral Movement: Exploring Internal Systems
Once administrative privileges are obtained, attackers expand their reach laterally across the organization’s network. This phase is about discovery and reconnaissance within internal systems.
They identify:
- Critical databases and file servers.
- Internal applications or cloud storage containing sensitive data.
- Security solutions and monitoring tools that could detect them.
Data Exfiltration & Persistence: Stealing Information and Maintaining Presence
In the final phase, the attackers focus on extracting valuable data – such as intellectual property, customer information, or trade secrets – while ensuring they can maintain long-term access.
- Data exfiltration often occurs in small, encrypted packets to avoid detection by network monitoring tools.
- Cloud storage services, DNS tunneling, or custom encryption protocols may be used to transfer stolen information outside the network.
- Simultaneously, attackers establish persistence mechanisms, such as hidden user accounts, scheduled tasks, or additional backdoors, ensuring they can return even after partial remediation.
Key Characteristics of APT Campaigns
Advanced Persistent Threat (APT) campaigns are defined by their strategic intent and sophistication. Unlike opportunistic cyberattacks that rely on quick hits for financial gain, APTs are methodical, patient, and tailored to the target’s ecosystem. They are often orchestrated by well-funded groups aiming to compromise high-value organizations such as government institutions, defense contractors, technology firms, or critical infrastructure operators.
Targeted and Goal-Oriented Attacks
APT actors don’t attack randomly. Their campaigns are meticulously planned against specific organizations or sectors, often with a clear objective – espionage, data theft, or disruption of operations.
They invest significant time researching the targets:
- Organizational hierarchy and key personnel.
- Network architecture and technology stack.
- Third-party dependencies and security measures.
Long-Term Infiltration with Minimal Detection
Persistence is the hallmark of an APT. Once an attacker gains a foothold, the objective is to remain undetected for months or even years, silently observing and exfiltrating data without triggering alerts.
APT groups use techniques such as:
- Rotating command-and-control (C2) infrastructures.
- Encrypting malicious traffic to mimic legitimate network behavior.
- Using “living off the land” tools like PowerShell, WMI, and legitimate admin utilities.
Customized Malware and Zero-Day Exploits
APT campaigns rarely rely on off-the-shelf malware. Instead, they develop custom payloads or zero-day exploits that evade antivirus signatures and intrusion detection systems.
Their tools are highly adaptable and modular, often featuring:
- Encrypted communication channels between infected hosts.
- Self-deleting scripts or fileless malware to minimize traces.
- Adaptive code behavior, enabling dynamic modification when defenses evolve.
Use of Social Engineering and Supply-Chain Vectors
APT attackers combine technical sophistication with psychological manipulation.
- Through spear-phishing, whaling, or fake business correspondence, they exploit human trust to deliver malicious payloads or steal credentials.
- Increasingly, APTs also exploit supply-chain vulnerabilities – compromising trusted vendors or third-party software updates to infiltrate multiple organizations simultaneously.
Notable APT Examples
Over the past decade, numerous Advanced Persistent Threat (APT) groups have conducted large-scale cyber operations with clear strategic, financial, or espionage goals. The following are verified, publicly attributed examples that have been analyzed and documented by reputable cybersecurity authorities and threat intelligence organizations.
APT28 (Fancy Bear): Espionage on European Defense and Media Entities
APT28, also known as Fancy Bear or Sofacy, is one of the most well-documented APT groups in the world. Public reports by FireEye, CrowdStrike, and MITRE ATT&CK attribute this group to long-term cyber-espionage campaigns targeting European military, political, and media institutions.
Key Characteristics:
- Utilizes custom malware families such as X-Agent, Sednit, and CHOPSTICK.
- Employs spear-phishing and credential harvesting techniques for targeted infiltration.
- Focuses on gathering intelligence from defense and government networks, with secondary emphasis on disinformation operations through media compromise.
Lazarus Group: Financial Cyberattacks Targeting Cryptocurrency and Banking
The Lazarus Group, widely linked to North Korea by multiple intelligence agencies and cybersecurity firms, represents one of the most financially motivated APT collectives. Their campaigns have evolved from espionage to large-scale cyber theft and ransomware attacks.
Notable Operations:
- Bangladesh Bank Heist (2016): Attempted theft of nearly $1 billion via SWIFT network manipulation.
- WannaCry Ransomware (2017): A global ransomware campaign affecting over 200,000 systems across 150 countries.
- Crypto Heists (2018-Present): Targeted cryptocurrency exchanges and DeFi platforms to bypass financial sanctions.
APT10 (Stone Panda): Widespread Data Theft Operations
APT10, also known as Stone Panda or MenuPass Group, has been publicly attributed to long-term cyber-espionage campaigns primarily focused on intellectual property theft from global corporations and managed service providers (MSPs).
According to verified reports by PwC, CISA, and FireEye, APT10 conducted one of the largest known cyber-espionage operations in recent history.
Key Characteristics:
- Targeted IT service providers to infiltrate downstream client networks – a technique later termed the “Cloud Hopper” campaign.
- Stole trade secrets, technical documentation, and R&D data from aerospace, manufacturing, and healthcare sectors.
- Used sophisticated malware such as Redbaldknight and PlugX, often disguised within legitimate remote administration tools.
Detecting and responding to APTs
Detecting an Advanced Persistent Threat (APT) is one of the greatest challenges in modern cybersecurity. APT actors operate quietly, blending their actions with normal network behavior while maintaining long-term access. Successful defense requires a combination of early detection, threat intelligence, and rapid incident response.
Below are key indicators, tools, and response strategies to help organizations identify and contain APT activity before significant damage occurs.
Indicators of APT Presence
APTs are designed to remain hidden, but subtle clues often reveal their presence. Security teams should stay alert for the following indicators of compromise (IOCs):
- Unusual Outbound Traffic: Unexpected data flows to unfamiliar external IPs or domains, especially during non-business hours, can indicate data exfiltration or command-and-control (C2) communication.
- Privilege Escalation Patterns: Continuous or unexplained changes in account privileges suggest attackers are attempting to gain administrative control.
- Persistent Network Connections: Long-lived or recurring connections between internal and external systems, particularly those bypassing standard VPN or proxy channels, are red flags.
- Multiple Authentication Failures or Logins from New Locations: These may point to compromised credentials or credential-stuffing attempts.
- Unrecognized Processes or Scheduled Tasks: APTs frequently use legitimate-looking processes or scheduled jobs to maintain persistence.
Tools and techniques
Effective APT detection relies on layered visibility across endpoints, networks, and cloud environments. Combining modern security technologies enhances both detection accuracy and response speed.
Endpoint Detection and Response (EDR)
EDR solutions continuously monitor endpoint activity for anomalies such as unauthorized registry edits, file manipulations, or process injections. They provide real-time alerts and detailed forensic data to trace attacker behavior.
Tools like Microsoft Defender for Endpoint, CrowdStrike Falcon, or SentinelOne help detect advanced persistence mechanisms and automate containment.
Threat intelligence feeds
Threat intelligence platforms aggregate real-world data on known malicious IPs, domains, malware hashes, and attacker tactics. Integrating these feeds into SIEM (Security Information and Event Management) systems enables proactive blocking and correlation of activity with known APT campaigns.
Reliable sources include CISA, MITRE ATT&CK, and SecureLayer7 Threat Intelligence Reports.
Network traffic monitoring
Continuous network visibility is crucial for identifying C2 communication and data exfiltration attempts. Technologies such as Network Detection and Response (NDR) or Deep Packet Inspection (DPI) can help detect encrypted tunnels, beaconing patterns, or data transfers that deviate from normal baselines.
Segmenting critical systems and analyzing east-west traffic (lateral movement) further reduces exposure.
AI/ML-based anomaly detection
Artificial Intelligence and Machine Learning systems analyze massive datasets to recognize patterns humans might miss. By learning what “normal” looks like within a specific environment, AI-driven platforms can detect deviations that signal an APT – such as unusual file access, unexpected system calls, or anomalous data transfer rates.
These tools greatly improve the speed and accuracy of threat detection, especially in large or hybrid infrastructures.
Response Steps: Containing and Eradicating the Threat
Once indicators of an APT are detected, swift and structured response is critical to prevent further compromise. The response process typically includes:
- Isolate Compromised Systems
- Immediately disconnect affected devices from the network to prevent lateral movement.
- Suspend compromised user accounts and revoke privileged access.
- Analyze Logs and Evidence
- Collect and preserve forensic artifacts – network logs, event data, and malware samples – for detailed investigation.
- Use correlation tools to trace the attacker’s path and understand the scope of intrusion.
- Eradicate Malware and Backdoors
- Remove malicious files, scripts, and registry entries.
- Patch exploited vulnerabilities, reset credentials, and updated security configurations.
- Strengthen Monitoring and Defenses
- Deploy continuous monitoring across endpoints and networks.
- Update detection rules, integrate threat intelligence indicators, and reinforce access control.
- Conduct post-incident reviews to identify gaps and improve response readiness.
Strengthening APT Protection Measures
Defending against Advanced Persistent Threats (APTs) requires more than just reactive detection – it demands a proactive, multi-layered security strategy. Since APT actors combine stealth, persistence, and social engineering, organizations must build a defense posture that anticipates threats, minimizes exposure, and rapidly responds to anomalies.
Below are essential strategies for strengthening APT protection measures across infrastructure, processes, and people.
Implement Multi-Layered Defense (Firewalls, IDS, EDR)
A defense-in-depth approach ensures that no single failure leads to compromise. Deploying multiple layers of security – from network perimeter to endpoints – helps detect and block threats at various stages of an APT attack.
- Next-Generation Firewalls (NGFW): Filter traffic based on deep packet inspection and application awareness.
- Intrusion Detection and Prevention Systems (IDS/IPS): Identify and stop suspicious activities in real time.
- Endpoint Detection and Response (EDR): Continuously monitor and analyze endpoint behavior to identify malicious processes or persistence mechanisms.
Adopt Zero Trust Principles and Strict IAM Controls
The Zero Trust Security Model operates on a simple principle – never trust, always verify. Every access request, whether internal or external, must be continuously authenticated and authorized.
Key actions include:
- Implementing Role-Based Access Control (RBAC) to ensure users only access what they need.
- Enforcing Multi-Factor Authentication (MFA) to prevent credential abuse.
- Adopting continuous verification and session-based access policies.
- Monitoring privileged accounts through Privileged Access Management (PAM) tools.
Apply Timely Patch Management and Vulnerability Scanning
Unpatched software and outdated systems remain one of the most common entry points for APTs. Organizations should establish a structured patch management policy supported by automated scanning and prioritization tools.
Best practices include:
- Regular vulnerability scans using tools like Nessus or Qualys.
- Maintaining a centralized inventory of all software and devices.
- Applying critical security patches promptly, especially for internet-facing applications and servers.
- Monitoring threat intelligence feeds for newly disclosed zero-day vulnerabilities.
Segment Networks to Limit Movement
Network segmentation helps contain breaches and limit an attacker’s ability to move laterally.
By dividing the network into smaller, isolated zones, organizations can restrict communication between systems unless explicitly authorized.
Key steps include:
- Separating production, testing, and administrative environments.
- Applying micro-segmentation to enforce granular controls between workloads.
- Implementing least privilege access between segments.
- Monitoring inter-segment traffic for unauthorized attempts.
Conduct Red-Team Assessments and Periodic Penetration Testing
Regular red-team simulations and penetration tests help evaluate how well your organization can detect and respond to real-world APT tactics.
- Red-Team Exercises: Simulate APT-style campaigns to assess detection, response time, and cross-team coordination.
- Penetration Testing: Identify exploitable vulnerabilities in networks, applications, and APIs. For a detailed breakdown of securing APIs and identifying attack vectors that often enable persistent access.
- Purple-Team Engagements: Encourage collaboration between offense (red) and defense (blue) teams to improve overall security maturity.
Train Employees to Recognize Phishing and Social Engineering Attempts
Human error remains one of the weakest links in cybersecurity. APTs frequently use spear-phishing, malicious attachments, and fake login pages to gain initial access.
To reduce this risk:
- Conduct regular security awareness training covering email hygiene, password safety, and data handling.
- Run phishing simulations to evaluate employee vigilance.
- Encourage a security-first culture, where employees promptly report suspicious emails or activities.
Role of Threat Intelligence and Collaboration
Defending against Advanced Persistent Threats (APTs) isn’t a solitary effort – it requires continuous intelligence sharing, global collaboration, and alignment with industry frameworks.
APT campaigns are sophisticated, adaptive, and often backed by well-resourced actors. To effectively counter them, organizations must leverage threat intelligence to understand attacker tactics and engage in collaborative defense ecosystems that pool collective insights and expertise.
Using Threat Intelligence to Recognize Known Attacker Patterns
Threat intelligence transforms raw data into actionable insights that help security teams identify and neutralize APT activity before it escalates. By analyzing threat indicators such as malicious IPs, domains, file hashes, and behavioral signatures, organizations can detect patterns that match known APT groups and stop them early in the attack chain.
Key benefits include:
- Early Warning: Real-time alerts about campaigns targeting your industry or region.
- Proactive Defense: Updated blocklists and correlation with your SIEM/EDR systems.
- Contextual Awareness: Understanding attacker motivations, tools, and typical entry points.
Leveraging Frameworks like MITRE ATT&CK for APT Behavior Mapping
The MITRE ATT&CK framework has become an industry-standard tool for understanding how APT groups operate. It provides a comprehensive, globally recognized knowledge base of tactics, techniques, and procedures (TTPs) observed in real-world attacks.
Organizations can use MITRE ATT&CK to:
- Map Detected Behaviors: Identify which APT tactics align with specific adversary groups (e.g., credential access, lateral movement, exfiltration).
- Assess Coverage Gaps: Evaluate which phases of the APT lifecycle your current controls fail to detect.
- Prioritize Defenses: Focus resources on techniques most likely to affect your environment.
Importance of Collaboration through ISACs, CERTs, and Security Vendors
No single organization can maintain complete visibility into all global threats. That’s why collaboration across industries and regions is critical for building collective resilience against APTs.
Key collaboration channels include:
- Information Sharing and Analysis Centers (ISACs): Industry-specific hubs (like Financial Services ISAC or Health ISAC) where members share threat data and best practices.
- Computer Emergency Response Teams (CERTs): National and regional teams (such as CERT-In, US-CERT, or ENISA CERT) that issue advisories, coordinate responses, and facilitate cross-sector communication.
- Security Vendors and MSSPs: Partnering with experts who provide up-to-date intelligence feeds, forensics, and response capabilities.
Conclusion
As the frequency and sophistication of Advanced Persistent Threats (APTs) continue to grow, enterprises face an ever-expanding risk landscape where traditional security tools are no longer enough. Modern adversaries leverage stealth, persistence, and advanced evasion tactics to infiltrate critical systems and remain undetected for months.
To stay ahead of evolving threats, organizations must strengthen every layer of their defense – from endpoint visibility and Zero Trust access controls to threat intelligence sharing and red-team testing.
Stay ahead of sophisticated cyberattacks. Partner with SecureLayer7 to enhance your organization’s resilience through continuous threat monitoring, penetration testing, and comprehensive APT defense solutions designed to protect your most critical digital assets.
Frequently Asked Questions (FAQs)
An Advanced Persistent Threat (APT) is a prolonged, targeted cyberattack where skilled threat actors infiltrate a network to steal data or conduct espionage over an extended period. These attacks are stealthy, strategic, and often backed by well-resourced groups or nation-state actors.
APT attacks typically unfold in multiple stages – gaining initial access (often via phishing or vulnerabilities), establishing a foothold, escalating privileges, moving laterally through the network, and exfiltrating data while maintaining long-term persistence.
APTs are dangerous because they operate silently and can remain undetected for months or years, giving attackers continuous access to sensitive information. Their persistence allows for deep infiltration, data theft, and potentially devastating financial or reputational damage.
APT groups commonly target government agencies, defense contractors, financial institutions, healthcare providers, energy companies, and technology firms – sectors that store valuable intellectual property or sensitive data.
Unlike regular cyberattacks that are quick and opportunistic, APTs are strategic, long-term operations. They use sophisticated techniques, custom malware, and intelligence gathering to achieve specific goals, making them far harder to detect and eliminate.



