SecureLayer7 Gratis PenTest Summer 2017
February 26, 2017How are work, life and things at SecureLayer7
July 11, 2017
Welcome to the seventh installment of our blog series on “Insufficient Attack Protection.” In this edition, we shine a spotlight on the growing concern of CAPTCHA bypass attacks, a well-known security mechanism used to protect websites from automated bots.
Despite being a widely used security measure, CAPTCHA is not foolproof, and cyber criminals have devised sophisticated techniques to circumvent it.
In this blog, we will explore the risks and implications of CAPTCHA bypass attacks, the methods employed by attackers, and best practices to strengthen its security.
Join us as we uncover the challenges and solutions to effectively defend against CAPTCHA bypass attacks and safeguard websites from malicious activities.
Before delving deep into the blog, let us shed some light on the basic concepts of CAPTCHA.
What is CAPTCHA?
CAPTCHA, or Completely Automated Public Turing test to tell Computers and Humans Apart, is a security measure used on websites and online platforms to distinguish between human users and automated bots.
CAPTCHAs typically involve challenges that are easy for humans to solve but difficult for bots, such as distorted text or images, puzzles, or object recognition tasks.
They are used to prevent bots from accessing or abusing online services, such as spamming, data scraping, or brute force attacks.
CAPTCHAs have evolved over time and may also incorporate behavioural analysis and contextual data to determine human or bot activity. While CAPTCHAs enhance online security, they can also be frustrating for users, especially those with disabilities.
Why is CAPTCHA Important?
There have been so many advancements to distinguish between robots and humans in the past few decades. CAPTCHA is one of the most effective and has its advantages to stay in this run.
Here are a few critical reasons why CAPTCHA is important
1. Security
CAPTCHA helps protect websites and online services from automated bots or scripts that attempt to perform malicious activities such as data scraping, brute-force attacks, or fraudulent activities.
By verifying that the user is human, CAPTCHA adds a layer of security to prevent unauthorized access and protect sensitive information.
2. User Verification
CAPTCHA is used to verify that the user attempting to access a website or service is a human and not a bot. This helps ensure that the intended audience is accessing the content or services, and prevents bots from abusing or exploiting online resources.
3. Preventing Spam
CAPTCHA is commonly used in online forms, such as registration forms, comment sections, and contact forms, to prevent spam submissions.
Bots often attempt to automatically submit spam messages, links, or advertisements to websites, and CAPTCHA helps differentiate between human users and automated bots, reducing the amount of spam received by websites.
4. Data Accuracy
CAPTCHA can be used to improve the accuracy of data collection efforts, such as digitizing books or transcribing audio recordings.
By requiring human input to solve CAPTCHA challenges, it helps ensure that the transcribed data is more accurate and reliable.
5. Accessibility
CAPTCHA is designed to be challenging for bots but still accessible for most human users. CAPTCHA solutions have evolved to include accessibility features such as audio challenges or alternative text options, making them usable for people with disabilities who may have difficulty with visual challenges.
6. Protection against data mining bots
Certain sites that contain a very large amount of data are vulnerable to data mining attacks. They need to protect themselves from such abuse and need a CAPTCHA implementation. Examples of such sites: are social networking sites and search engines.
7. Protecting against authentication-related attacks
Certain functionalities are needed to be protected against brute force attacks. For example:
- Login: Account takeover can be performed by guessing the right credentials.
- Forgot password: Username enumeration can be performed if the web app responds with a verbose message stating whether the account exists or not.
- Registration: Fake accounts can be created. Also, username enumeration can be performed because no application will allow two users to choose the same username.
8. Avoiding SPAM and DOS
Some functionalities require users to submit the form , which is later approved by the site administrator.
Examples of such are: applying for a membership, contacting us, feedback forms, surveys, etc. These need to be well protected against bots.
If not, it will lead to:
- Fake request creation: Fake requests will be created that will cause overhead for the site administrator. The site admin will need to go through forms submitted by bots and humans, so legitimate users will be denied service and he will also be denied service.
- Email bombarding: Some functionalities send emails to an arbitrary email address. These are also often targeted if not well protected by CAPTCHA. Thus an attacker can, on behalf of the web app, send numerous emails to internet users.
Why does the CAPTCHA get bypassed?
Despite having so many advantages, CAPTCHA still has some loopholes that can be leveraged to break through accessibility.
We have listed two main reasons why CAPTCHA gets bypassed. We will also get into the functionality of breaking into the accessibility for these two reasons so that we can be prepared for an actual attack.
With that said, CAPTCHA is bypassed due to two reasons:
- Design Issues
- Implementation Issues
1. Design Issues
Design issue refers to the stage where the design of the CAPTCHA is weak but the implementation is alright.
Let us explore some hands-on experiences by cracking one such CAPTCHA with the help of a weaker design.
- Design Issues #1
This CAPTCHA is nothing more than an arithmetic operation that the user will have to perform to move ahead. The mathematical question is in the HTML source code of the same page on which CAPTCHA is presented.
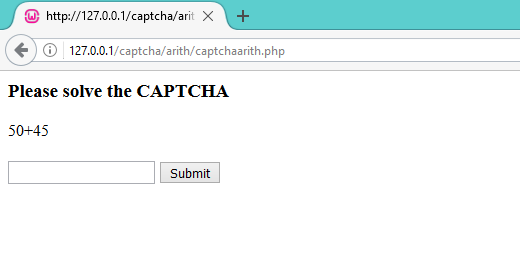
For reference, you can also download the source code of this CAPTCHA from here.
How to Crack This CAPTCHA?
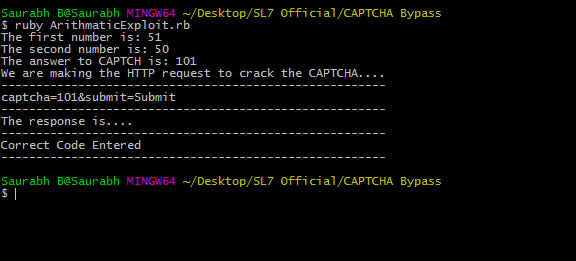
All the attacker has to do in this case is to fetch the source code, compute the answer and submit the HTTP Response to crack the CAPTCHA.
For reference, you can download this exploit code from here.
- Design Issue # 2
This CAPTCHA has a limited database of questions. It is an image-based CAPTCHA that cannot be cracked by reading the HTML source code and then computing the answer and submitting it.
But the problem lies in the limited number of questions.
In the below CAPTCHA, there are only 10 challenges that keep iterating, thus making it vulnerable.
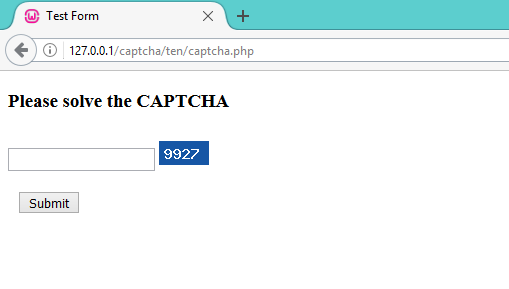
For reference, you can download this CAPTCHA code from here.
How to Crack this CAPTCHA?
The attacker has to manually once solve the 10 CAPTCHA questions. and at the same time has to note down answers to corresponding questions. After that, a tool can be made to keep on cracking them constantly. The tool fetches the questions looks for the answer in its own database and then cracks it.
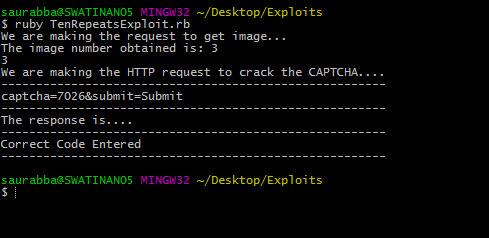
For reference, you can download this exploit code from here.
2. Implementation Issues
The implementation issue refers to the state of CAPTCHA, where the design of the CAPTCHA is perfect but the implementation is weak.
Let us have a closer look at the implementation issues and how to crack them.
- Implementation Issue # 1
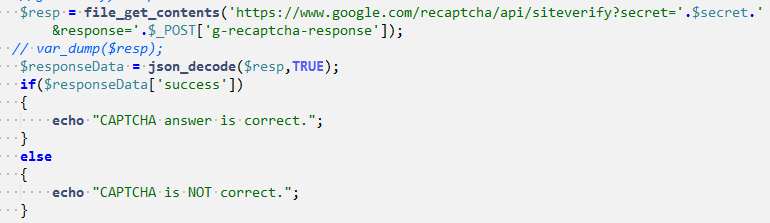
In this demo, we are using Google reCAPTCHA. We use an API that sends the response of CAPTCHA solved by the user to Google’s endpoint. More about this reCAPTCHA here. The API replies to the request in the form of JSON output, along with an HTTP Status code.
But the implementation issue arises here because the developer fails to check the JSON response. Instead, he checks the HTTP Status code, which is sent as 200 OK, for correct and incorrect CAPTCHA responses both.
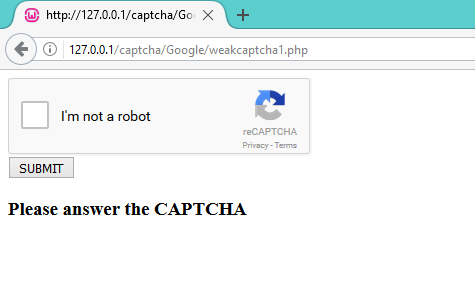
For reference, you can download this CAPTCHA code from here.
Note – In the above scenario, a bug was submitted in a bug bounty program. It was accepted and the security team told that they implemented their CAPTCHA in this particular way i.e. they only checked the status code and not the JSON response.
How To Crack this CAPTCHA?
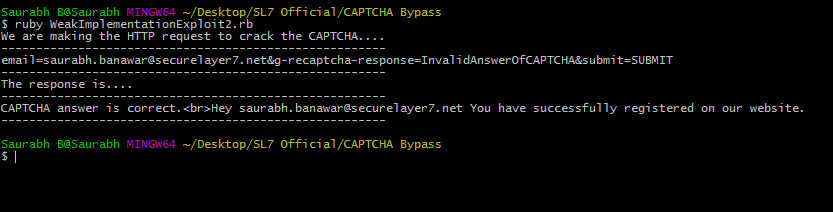
The attacker simply has to make a script that will send any value to CAPTCHA and the server will accept it because no matter what answer you sent, the server will only check whether the status code sent by Google API is “200 OK” or not (It will be always be “200 OK”.
In the below image, the value we are sending as an answer is ‘InvalidAnswerOfCAPTCHA’
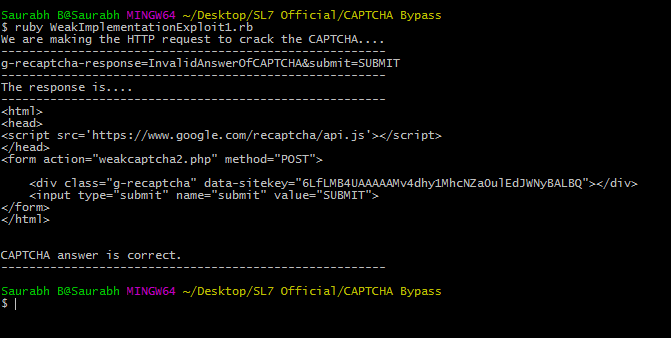
For reference, you can download this exploit code from here.
- Implementation Issue # 2
This CAPTCHA is present on the web page. It has been validated after submission. But, a simple if and else clause makes it vulnerable.
The error occurs when the developer includes a positive response code in the “else” section. Even if the CAPTCHA solution is incorrect, the programme will respond positively to the user.
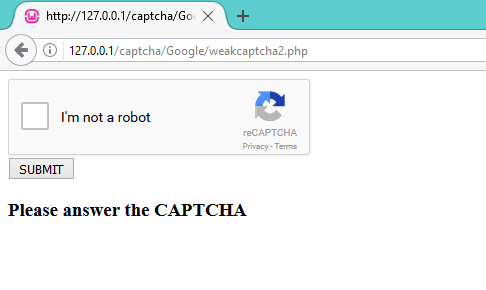
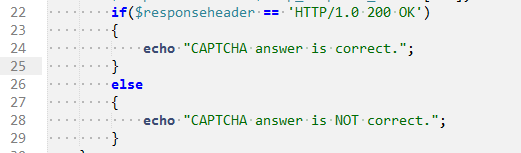
For reference, you can download this CAPTCHA code from here.
How to Crack this CAPTCHA?
To crack this CAPTCHA, the attacker simply has to make a script that will send any value to CAPTCHA. In the below image, the value we are sending as an answer is ‘InvalidAnswerOfCAPTCHA’
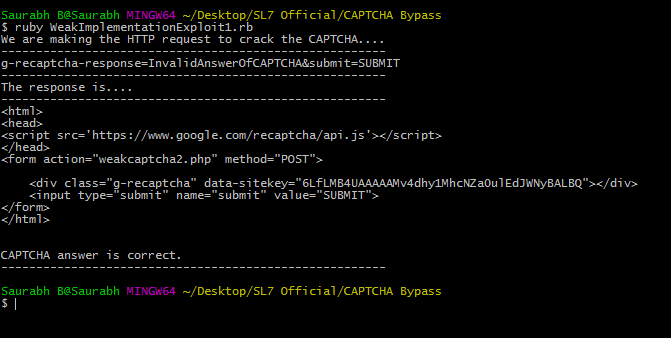
For reference, you can download this exploit code from here.
- Implementation Issue # 3
This CAPTCHA is present on the web page, but after it has been submitted, it never got validated on the server side.
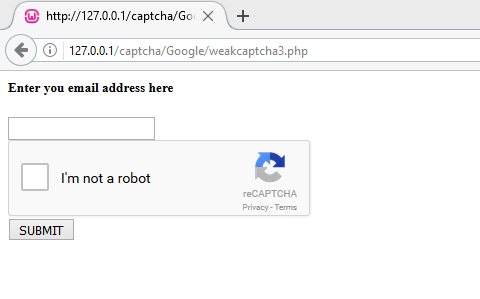
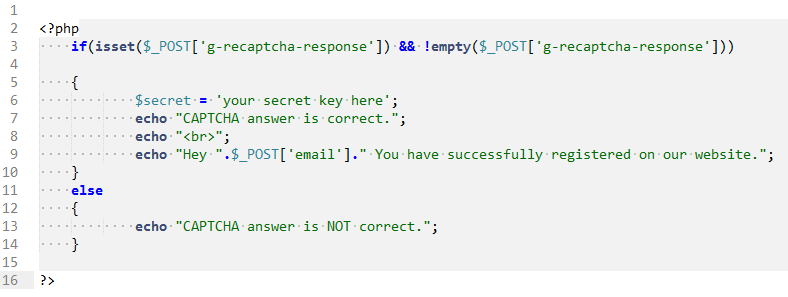
For reference, you can download these CAPTCHA codes | CAPTCHA from here.
How to Crack this CAPTCHA?
So, by simply entering the wrong CAPTCHA answer and an arbitrary value of email, an attacker can bypass it.
For reference, you can download this exploit code from here.
How to protect ourselves from CAPTCHA attacks?
The solution to this is very simple. Follow these steps in making a strong CAPTCHA functionality:
- Design: Implement a CAPTCHA which is good in design. We have seen how self-made designs can be vulnerable. So use a third-party CAPTCHA service provider like Google.
- Implementation: After you have chosen a CAPTCHA with a good design, the next step is to implement it correctly. We have seen that despite having a CAPTCHA with a good design, it can still be cracked if not implemented correctly. If you are using Google reCAPTCHA then follow these steps:
- Do not check the validity of the answer by HTTP Status code, instead check the JSON response sent by Google.
- Implement proper logic in the if and else clause which differentiates between valid and invalid answers.
- Do not disclose your private CAPTCHA key. It is a secret.
You can download this secure CAPTCHA code from here.
Takeaways
In conclusion, protecting web applications from CAPTCHA bypass attacks is crucial in today’s threat landscape.
As the OWASP TOP 10 list indicates, insufficient attack protection, specifically CAPTCHA bypass, is a significant vulnerability that can be exploited by malicious actors.
A proactive approach to CAPTCHA protection, in combination with other security best practices, can significantly enhance the overall security posture of web applications, safeguard sensitive data, and provide a secure online experience for users.


